Emotet Is now Distributed via Microsoft OneNote Files
The well-known Emotet malware, which has recently resumed its activity, is now distributed via emails with Microsoft OneNote attachments. Thus, the malware seeks to bypass the restrictions associated with disabling macros in Microsoft Word and Excel and infect more targets.
Let me remind you that we also wrote that Emotet steals attachments from victims’ emails, and also that Unknown hackers interfere in the work of the Emotet botnet by replacing malware with GIF files.Let me remind you that recently Emotet resumed work after a three-month break and again began sending malicious emails around the world. However, at first, malware operators, as usual, tried to use Word and Excel documents with macros for attacks.
Since Microsoft now automatically blocks macros in documents downloaded from external sources (including email attachments), this campaign was unlikely to be successful.
As many information security experts predicted, Emotet has now switched to using Microsoft OneNote to get around these limitations. As part of the new campaign, Microsoft OneNote documents are attached to emails and display a message that the document is protected. The potential victim is prompted to double-click on the “View” button to display the document correctly.
The fact is that Microsoft OneNote allows creating documents containing various design elements that are superimposed on an embedded document. As a result, when you double-click on the place where the embedded file is located (even if there is a design element above it), the file will be launched. And in this malicious campaign, Emotet operators have hidden a malicious VBScript file called click.wsf right below the View button.
VBScript contains an obfuscated script that downloads a DLL from a remote (probably compromised) site and then executes it by running the DLL with a random name using regsvr32.exe.
Although Microsoft OneNote displays a warning when a user tries to run an embedded file in OneNote, many users have been known to click the OK button without reading the warnings.
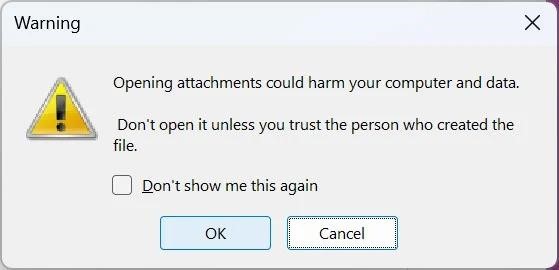
As a result, Emotet will work on the victim’s device, stealing email, contacts and waiting for further commands from the control server. While it is not known what payloads end up being delivered to the victim’s system as part of this campaign, infection usually results in the installation of Cobalt Strike or additional malware.





