Over 600,000 GPS trackers use default passwords and are available to everyone
Avast experts found that more than 600,000 GPS trackers used to monitor the location of children, the elderly, pets, cars and so on use the default password – “123456”.
Using the default password to crack users’ accounts, attackers can overhear conversations next to the GPS tracker, fake the real location of the device, and also find out the number of the SIM card attached to the tracker.It all started with detecting problems in the T8 Mini trackers made by the Chinese IoT company Shenzhen i365-Tech. However, experts soon found out that the password “123456” was also used for 30 other models of GPS trackers produced by the same company, some of which were sold as white-label devices and presented on the market under the brands of other companies.
All problematic trackers have the same infrastructure, which consists of a cloud server, which the tracker “reports” to, a web panel (which clients use via browsers to check the location of the device), as well as a similar mobile application that also connects to the same cloud server.
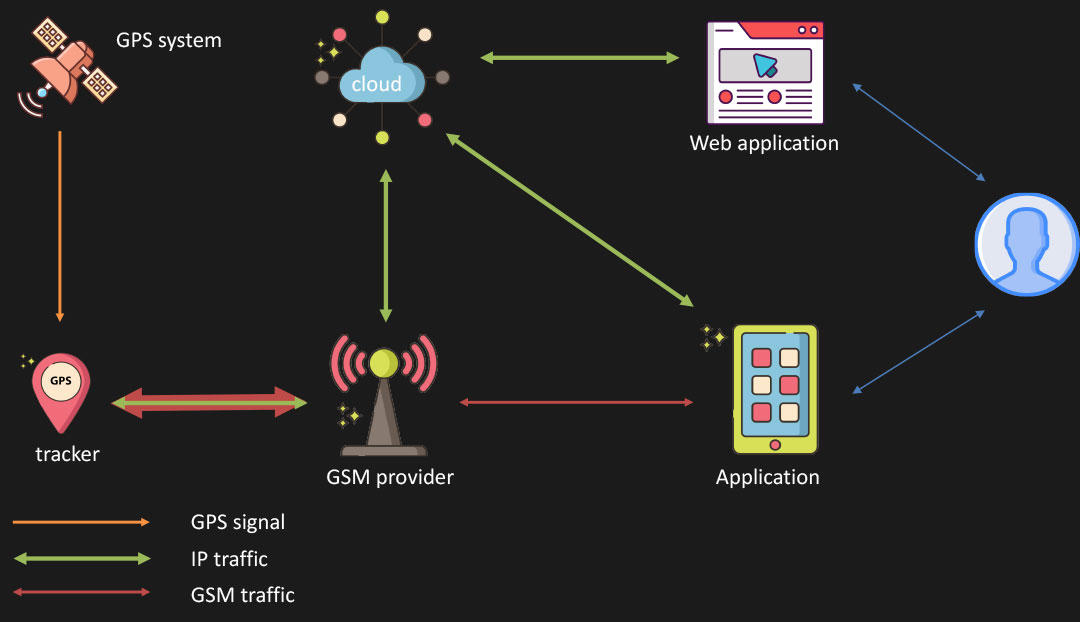
Although Avast experts immediately identified a number of problems in the described infrastructure, the biggest of them is the fact that all user accounts (both in the mobile application and the web panel) use a user ID and password, which are easy to pick up. Therefore, the user ID based on the IMEI of the tracker and is sequential, and the password, as mentioned above, is by default the same for all devices – this is “123456”.
“In fact, this means that attackers can launch an automated attack on the Shenzhen i365-Tech cloud server, iterating over all user IDs one by one and using the same password to crack user accounts”, – report in Avast.
Fortunately, users are not prohibited from changing the password for GPS trackers, however, Avast analysts scanned more than 4,000,000 identifiers and found that over 600,000 accounts still use the default password. The actual number of GPS trackers with default passwords is likely to be much higher.
Read also: Hackers stole 1.5 million euros from a German bank by cloning customer EMV cards
Moreover, the problem is compounded by the fact that such devices are equipped with built-in microphones and SIM cards so that children and older people can make SOS calls and communicate with their family members. The researchers found that compromising the tracker would actually allow attackers to make phone calls to their numbers, answer these calls, and then spy on the owner of the trackers.
Vulnerabilities found also threaten the manufacturing company itself. The fact is that vulnerable accounts are created in the cloud immediately after the manufacture of GPS trackers. Theoretically, a competitor could take control of these accounts even before the devices were sold and change passwords, thereby effectively blocking accounts and creating problems for Shenzhen i365-Tech and resellers.
All the problems described by experts are still relevant, since the representatives of Shenzhen i365-Tech did not respond to the numerous requests of researchers. Avast analysts strongly recommend that users of vulnerable trackers immediately change their passwords. A complete list of vulnerable devices is provided at the end of the expert report.