Researchers Discovered Dangerous Vulnerabilities in Devices that Distribute Wi-Fi on Airplanes
Researchers from Necrum Security Labs have identified two dangerous vulnerabilities in the Flexlan FX3000 and FX2000 devices, which are often used by Wi-Fi distributions on board of passenger airplanes.
They are manufactured by the Japanese company Contec, which specializes in embedded devices, industrial automation and IoT communication technologies.
See also: Symantec: Booking hotels and online check-ins on flights are unsafe.
The first issue, CVE-2022-36158, is related to a hidden web page that can be used to execute Linux commands on a device with root privileges. It is emphasized that the device management interface does not contain a direct link to this hidden page.
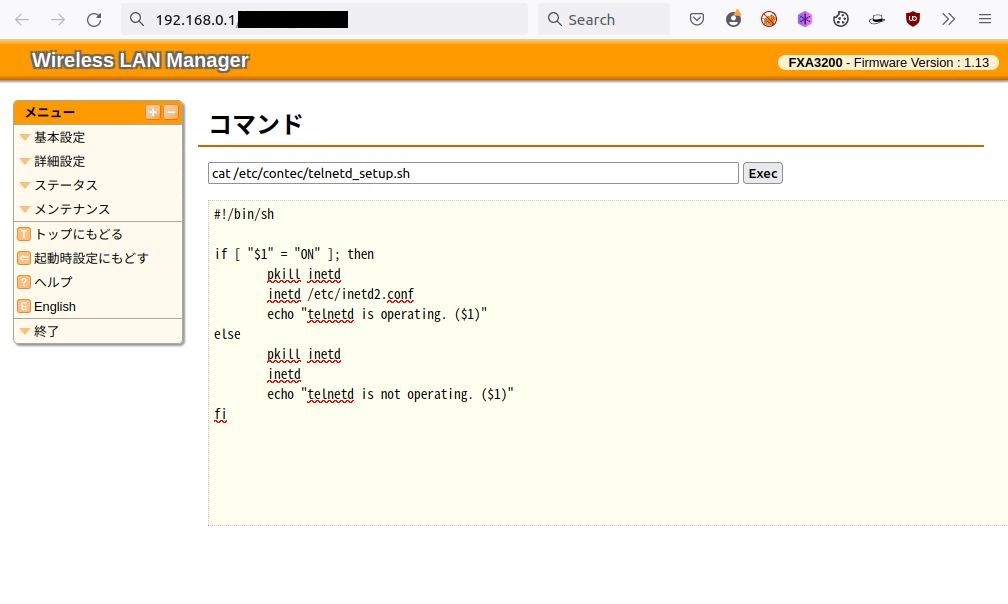
The second vulnerability, CVE-2022-36159, is essentially a backdoor. The fact is that the researchers found on the devices a root user account with a hard-coded default password. They assume that this account was originally intended for device maintenance.
The password in this case was stored as a hash, but experts easily cracked it, and they write that an attacker can use this account to take full control of the device.
While Contec reports that Flexlan wireless LAN devices are ideal for use in distribution systems, factories and offices, researchers say the devices are often used on aircraft to serve as Wi-Fi hotspots that passengers can use to connect to Internet and in-flight services.
Experts say that the discovered vulnerabilities can be exploited by a simple passenger, since the vulnerable interface is available to anyone. With it, an attacker can, for example, collect data from other passengers or infect their devices with malware.
Contec developers have already released patches for the problems described by Necrum Security Labs: firmware 1.16.00 for FX3000 series devices and 1.39.00 for FX2000 series devices eliminate vulnerabilities. In a security bulletin, the company says that exploiting the bugs could lead to “data borrowing, falsification and disruption of the system.analysts argue.