AvosLocker ransomware operators auction victims data
Journalists from The Record noticed that AvosLocker malware operators have created a special system on their website, with the help of which they auction the data of their victims if they refused to pay the ransom.
The AvosLocker group uses the now classic double extortion tactics. That is, criminals not only encrypt the data of their victims, but also publish files stolen from companies if they refuse to pay the ransom.This approach was first used by operators of the Maze ransomware at the end of 2019, when the group began to steal files from compromised companies before encrypting them. Now practically all extortionate groups operate in this way.
AvosLocker was no exception: the group, first discovered in July 2021, also used this scheme, and in the summer of 2021 posted on their website the details of several victims who refused to pay or negotiate after the attack.
But in mid-September, the hackers launched a redesigned version of their site, which now has a new auction feature.
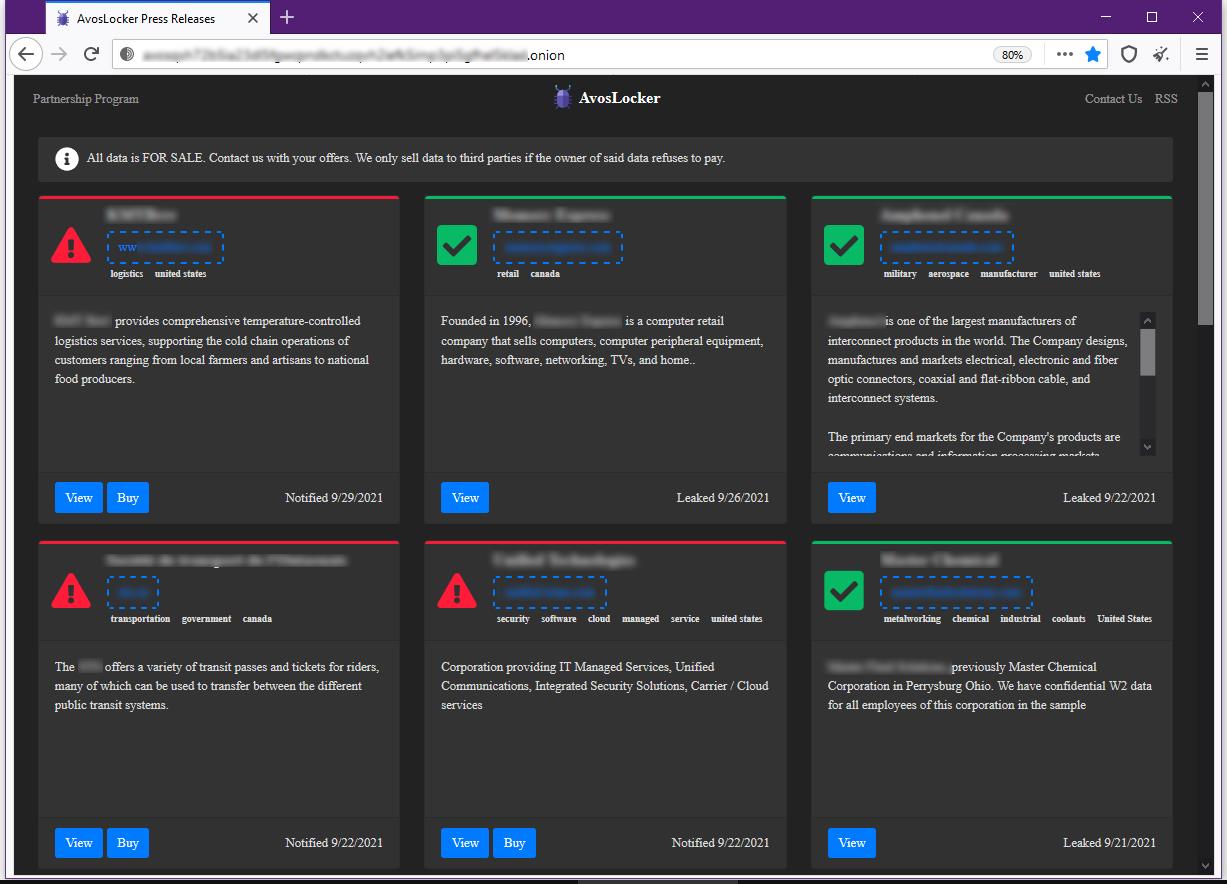
Now hackers do not “leak” information stolen from victims for free, but sell this data at auction, trying to profit even from unsuccessful attacks. Journalists note that this is a smart move, the fact is that the data published for free by the ransomware is then regularly resold in Telegram channels and on underground forums.
It should also be said that AvosLocker is not the first hack group to add auction functionality to their site. Most likely, the hackers were inspired by the experience of the ransomware REvil, which first used this tactic in June 2020.
Let me remind you that we talked about the fact that Hackers stole the source codes of Puma’s applications.





