Vulnerability in the video conferencing platform Zoom endangered more than 4 million Mac owners
Security researcher Jonathan Leitschuh revealed information about a serious vulnerability in the Zoom video conferencing service, through which attackers can remotely execute arbitrary code on the target system.
The researcher also calculated that more than 4 million users might encounter the problem.“As of 2015 Zoom had over 40 million users. Given that Macs are 10% of the PC market and Zoom has had significant growth since 2015 we can assume that at least 4 million of Zoom’s users are on Mac. Tools like Zoom, Google Meet or Skype for Business is a staple of today’s modern office”, — says Jonathan Leitschuh.
The problem related to one of the functions in Zoom, which automatically activates the application, allowing participants to join the video conference by clicking on the invitation in the browser.
As it turned out, Zoom installs a web server (port 19421) on the system, which receives commands via HTTPS GET requests, and any site opened in the browser can interact with the server. To compromise an attacker, you only need to create an invitation link in your account on the official Zoom website, embed it in a third-party resource (image or iFrame) and convince the user to visit this resource.
If the owner of the Mac, on which the Zoom software is installed, visits a malicious website, the application start automatically the computer and activate the webcam, putting the user at risk of attacks.

“Additionally, if you’ve ever installed the Zoom client and then uninstalled it, you still have a localhost web server on your machine that will happily re-install the Zoom client for you, without requiring any user interaction on your behalf besides visiting a webpage. This re-install ‘feature’ continues to work to this day. Yep, no joke”, — reports Jonathan Leitschuh
So, Zoom deinstallation will not be help to address an issue.
Aside from camera activation, an attacker can use this vulnerability for disabling Mac, simply by sending huge number of repeating GET requests on local server.
Researcher informed the developer of the platform about the problem, but after 90 days, Zoom did not eliminate the vulnerability. Ultimately, Leitschuh noted, Zoom partially fixed the bug by disabling the ability to activate the camera, but the problem that allowed the attacker to force the malicious site to attend the conference is still relevant.
“This is essentially a Zero Day. Unfortunately, Zoom has not fixed this vulnerability in the allotted 90-day disclosure window I gave them, as is the industry standard. As such, the 4+ million users of Zoom on Mac are now vulnerable to an invasion of their privacy by using this service”, — says Jonathan Leitschuh.
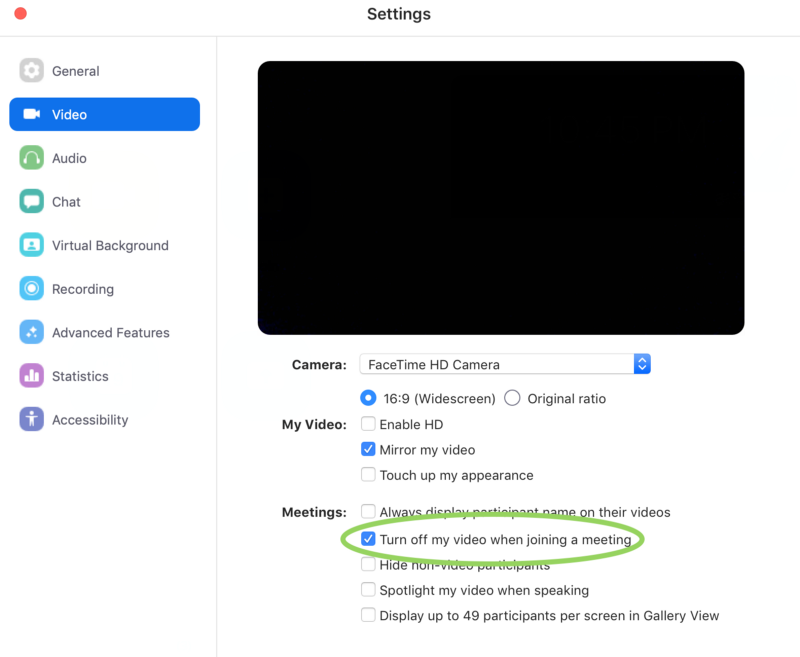
The abovedescribed vulnerability affects the latest version of Zoom (4.4.4) for macOS. Fortunately, users can solve the problem on their own by disabling the option in the Zoom settings that automatically activates the camera when connected to a video conference.






One Comment