Malwarebytes experts have discovered a cyber espionage hack group that uses the functionality of Windows Error Reporting (WER). Attackers use the WER to conduct fileless attacks.
In general, using WER to bypass security is not a new tactic, but now it seems that some new hack group is using it.
“The attackers hacked into the site where they eventually placed their payloads and used the CactusTorch framework to conduct a fileless attack using several anti-analysis methods”, — the researchers write.
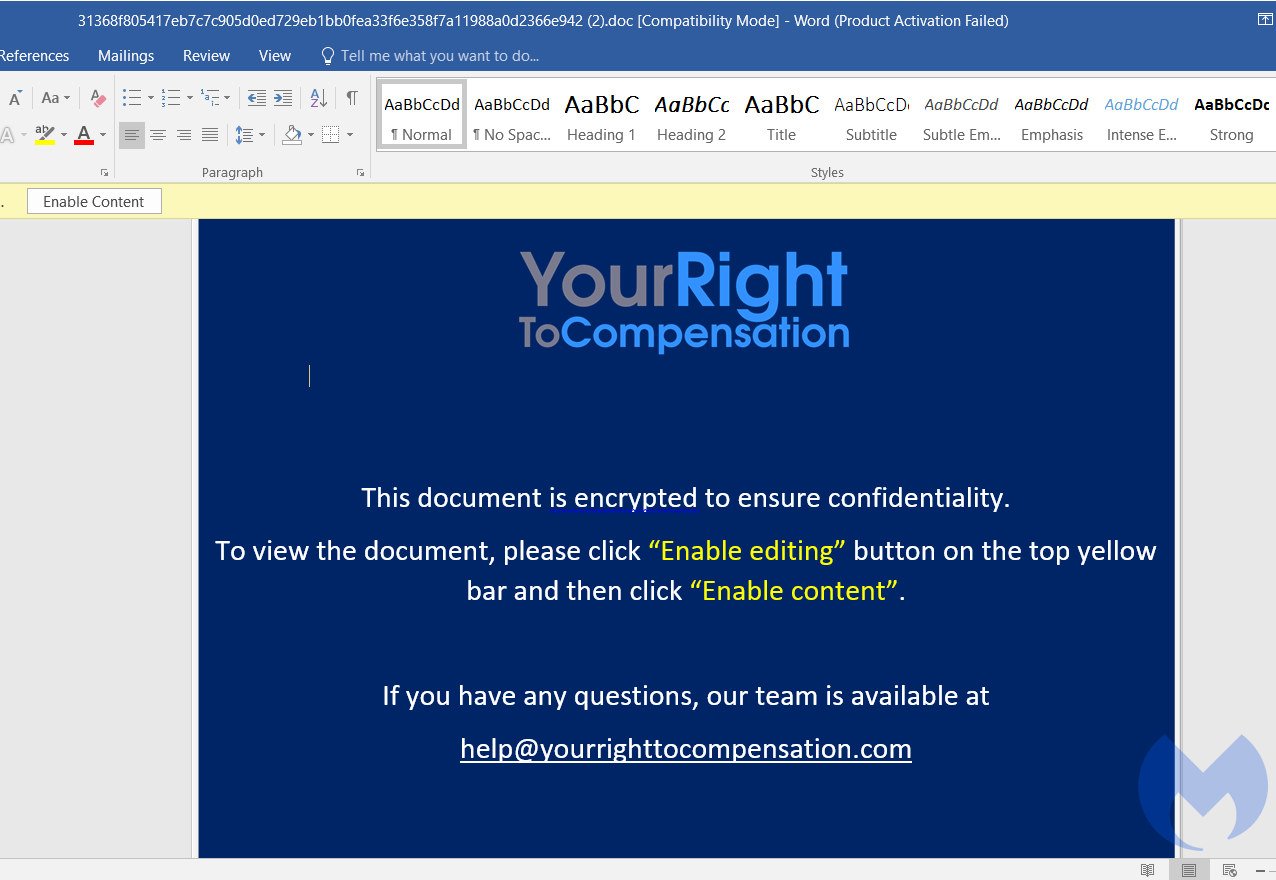
The attack was noticed on September 17 this year, when analysts discovered phishing emails containing a malicious document in a ZIP archive. That is, the initial payload reached the victims’ computers through targeted phishing, where documents related to the payment of compensation acted as decoys.
If the victim opened such a document, was triggered a malicious macro that was responsible for executing the shell code (a special version of the CactusTorch VBA module). It, in turn, used the DotNetToJscript technique and loaded the payload into the .NET device memory. The binary ran in the computer’s memory, leaving no traces on the hard drive, and injected shell code into WerFault.exe, a Windows process for the WER service.
It is noted that a similar injection method is used to evade detection by other malware, including the Cerber ransomware and NetWire RAT.
The Windows Error Reporting service, which is injected with malicious code, undergoes a series of anti-analytics checks to detect signs of debugging, virtual machine, or sandboxing. If all checks are passed, the malware will proceed to the next step: it will decrypt and download the final sell code, as well as the payload from the asia-kotoba[.]net site.
As a reminder, Malwarebytes researchers recently discovered that hackers hide web skimmers in image metadata.
“Unfortunately, this time we were unable to examine the final payload because the URL was not available when we analysed the attack“, — told Malwarebytes researchers.
While experts could not confidently attribute these attacks to any particular hacking group, some indicators and tactics used by the attackers point to the Vietnamese cyber espionage group APT32 (aka OceanLotus and SeaLotus), particularly known for attacks on BMW and Hyundai.
For example, APT32 previously used the CactusTorch VBA module to distribute Denis RAT malware. In addition, the domain yourrighttocompensation[.]com, registered in Ho Chi Minh City, Vietnam, was used to host and deliver phishing documents and malicious payloads in a recent campaign.
I think it will be interesting for you to read another story about cyber espionage: the creation of the Chinese Comac C919 aircraft was accompanied by hacker attacks and cyber espionage.





