A group of scientists from universities in Switzerland, Italy and the Netherlands said that the Android OS allows third parties to receive lists of all applications installed on the device.
Experts are preparing to present an interesting report at MOBILESoft, which will be held in Seoul this year, unless of course this is possible during the pandemic. However, the Pwn2Own contest was held in a virtual environment, and it seems that the same scenario is likable for the largest IT exhibitions and conferences.Experts’ report is already available on the network and is dedicated to the use of the little-known Android function, which may pose a threat to user privacy.
“Many Android applications use the IAM (Installed Application Methods), a set of Android API calls that allow developers to get a list of other applications installed on the user’s device”, – say the experts.
Initially, Google engineers created these API calls so that developers could detect application incompatibilities or customize interactions with other products. However, according to researchers, IAM is more often used to track and identify users. So, having studied the list of installed applications, the advertiser can collect information about the interests and personal qualities of a person (gender, languages, religious beliefs, age groups, and so on).
“Worse, it’s almost impossible to defend against snooping through IAM, because for it, the application does not need to request permission from the user. Moreover, application developers themselves may not suspect the use of IAM if they use third-party analytic packages or advertising libraries in their product. Those can silently make IAM API calls, and the developer will not even know about it”, – said the experts.
The published document says that the research team analyzed thousands of Android applications and their code in search of IAM API calls (regardless of whether the application code or a third-party library code was responsible for these calls). Thus, 14,342 applications from the tops of the Google Play Store were analyzed, as well as a set of 7,886 applications source codes of which were published on the Internet.
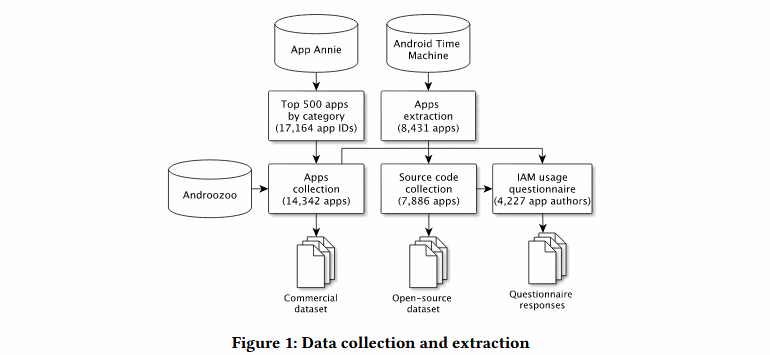
It turned out that the use of IAM is common among commercial applications: 30.29% (4,214) of Play Store applications make IAM calls. For open source applications, this number was only 2.89% (228 applications).
Researchers also tried to find out why applications even try IAM calls and what they are trying to achieve in this way. So, almost half of all fixed IAM calls detected by both applications from the Play Store and open source applications were used to call packageName IAM, which retrieves a list of locally installed applications.
The remaining IAM calls are rarely used (less than 15%, and in most cases less than 1%) and majority of them are IAM calls to obtain technical information about the application, such as signature, version, last update time, or SDK version numbers. Such calls are often used for debugging, for which the IAM API was originally created.
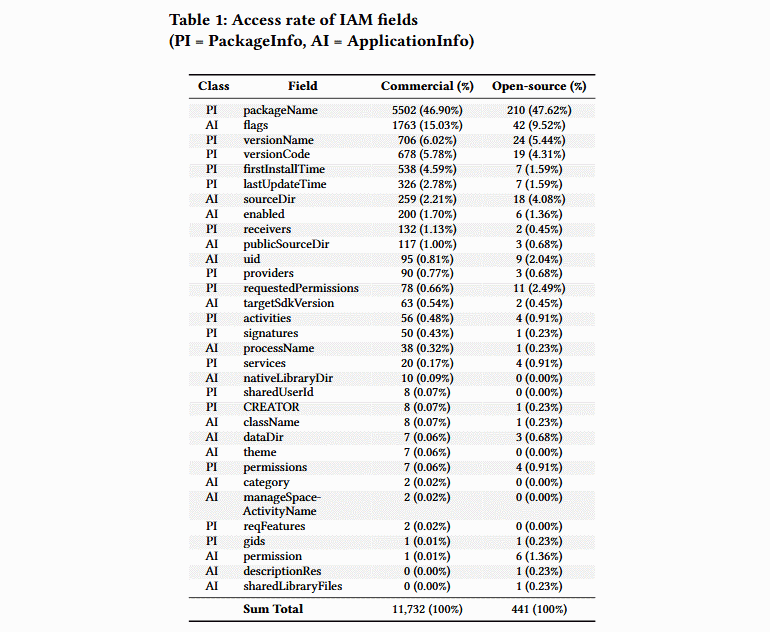
Researchers finally made sure that IAM calls are most often used for data collection, and not for debugging, when they checked where is located the code that usually performs these calls. Therefore, the vast majority of IAM calls come from third-party libraries, and not from the applications themselves.
“A total of 7,538 and 287 IAM calls were detected in commercial and open source applications (some applications make more than one call). The use of IAM in third-party libraries is more common in commercial applications, where 6,306 (83.66%) calls are made in the code belonging to the libraries, and the remaining 1232 (16.34%) are made in the native application code. As for open source applications, 178 calls (62.02%) were made by libraries, and the remaining 109 (37.98%) belong to their own application code”, – write the experts and add that more than a third of third-party libraries that made calls IAMs are used for promotional purposes.
At the conclusion of his report, the research team called on Android developers to limit the use of IAM API calls. According to experts, the ideal way out of the situation would be to request permission to work with IAM from users.
Well, this one more stone in Android, which was recognized as the most vulnerable platform over the past year.