An information security specialist published an exploit and information about a new vulnerability in UPnP, which allows arranging DDoS and is called CallStranger.
The problem allows attackers to take control of various “smart” devices, use them for DDoS attacks, as well as to bypass security solutions, scan the victim’s internal network and steal data.The vulnerability is associated with a set of UPnP network protocols, which these days can be found on most smart devices.
CallStranger problem was discovered in December 2019 by information security researcher Yunus Çadirci. He explains that the problem is similar to SSRF: an attacker can send TCP packets to the remote device that contain a malformed callback parameter in the header for the SUBSCRIBE function.
“Using CallStranger, the hacker aims to “look ”at the device’s Internet interface, but code execution uses the device’s UPnP functionality, which usually works only on internal ports, that is, inside the local network”, – explained Yunus Çadirci.
The distorted header can be used to attack any devices connected to the Internet and supporting UPnP, including surveillance cameras, DVRs, printers, routers, and much more. In particular, Chadyrdzhi writes that the problem extends to Windows PCs, game consoles, TVs and routers made by Asus, Belkin, Broadcom, Cisco, Dell, D-Link, Huawei, Netgear, Samsung, TP-Link, ZTE and so on.
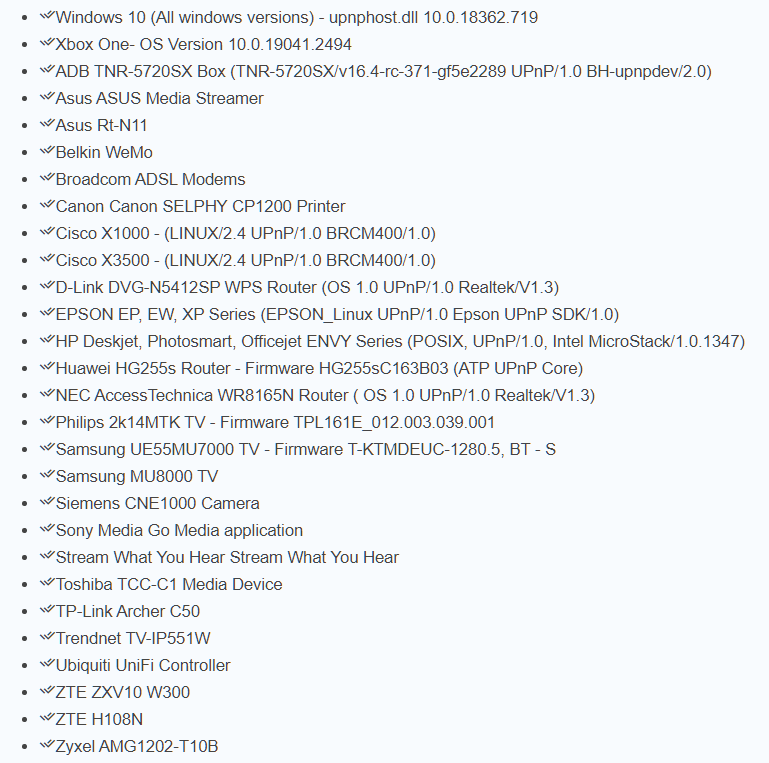
CallStranger has several applications. So, attackers can use CallStranger to bypass security solutions and firewalls, as well as scan internal company networks. Moreover, the problem can also be used to organize DDoS attacks (an attacker can increase TCP traffic using UPnP devices with Internet access) and data theft.
An Open Connectivity Foundation has already updated the specifications for UPnP protocols.
CERT/CC warns that not all buyers can apply these corrections in practice. The experts at CERT/CC and Chadirji agree that a final solution to the problem can take a very long time.
Currently, according to the search engine, Shodan can find 5.4 million devices with UPnP support, which could suffer from attacks by hacker groups and become members of the botnet.
UPnP allows devices to see each other on local networks, and then establish a connection, exchange data, settings, and so on. Since 2016, the Open Connectivity Foundation has been developing and standardizing the protocol suite.
Recall that recently, China declared a real war on DDoS services, and game maker Ubisoft coped with DDoS attacks from … off-line.





