Number of unique cyberattacks decreased for the first time in several years
Positive Technologies experts studied the current cyber threats in the third quarter of 2021 and reported that the number of unique cyber attacks has decreased. They also recorded an increase in the share of attacks on individuals, and an increase in the number of attacks on organizations using malware for remote control.
According to the analysis, in the third quarter of this year, the number of attacks decreased by 4.8% compared to the previous one.The company’s specialists have noted negative dynamics since the end of 2018. In their opinion, this is due to the reduction in the number of ransomware attacks and the departure of some major players from the scene. For the same reason, the share of attacks aimed at compromising corporate computers, servers and network equipment also decreased (from 87% to 75%).
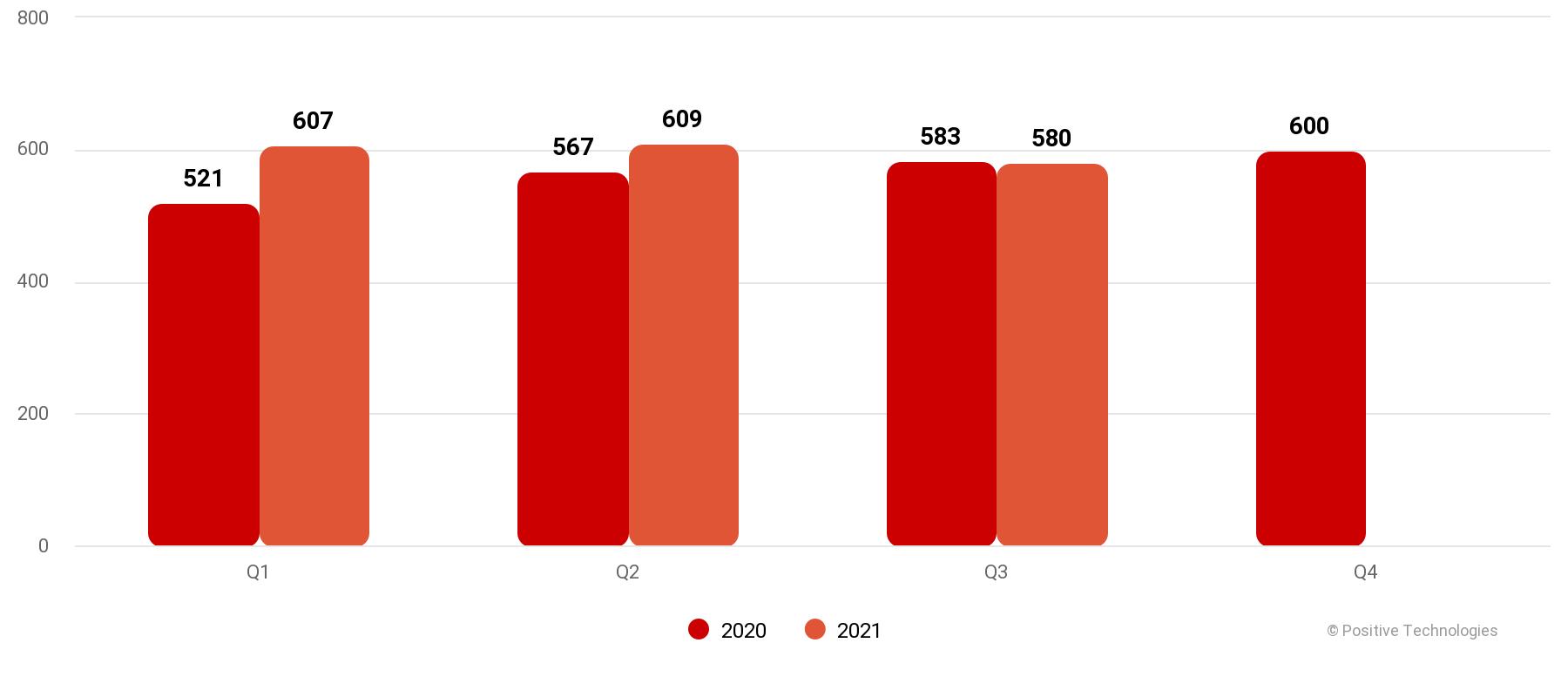
Number of incidents in 2020 and 2021 (by quarters)
Positive Technologies also noted a trend towards the so-called rebranding of existing ransomware, which involves some ransomware operators reconsidering their attitude to the ransomware as a service (RaaS, ransomware as a service) scheme, which carries certain risks from unscrupulous partners.
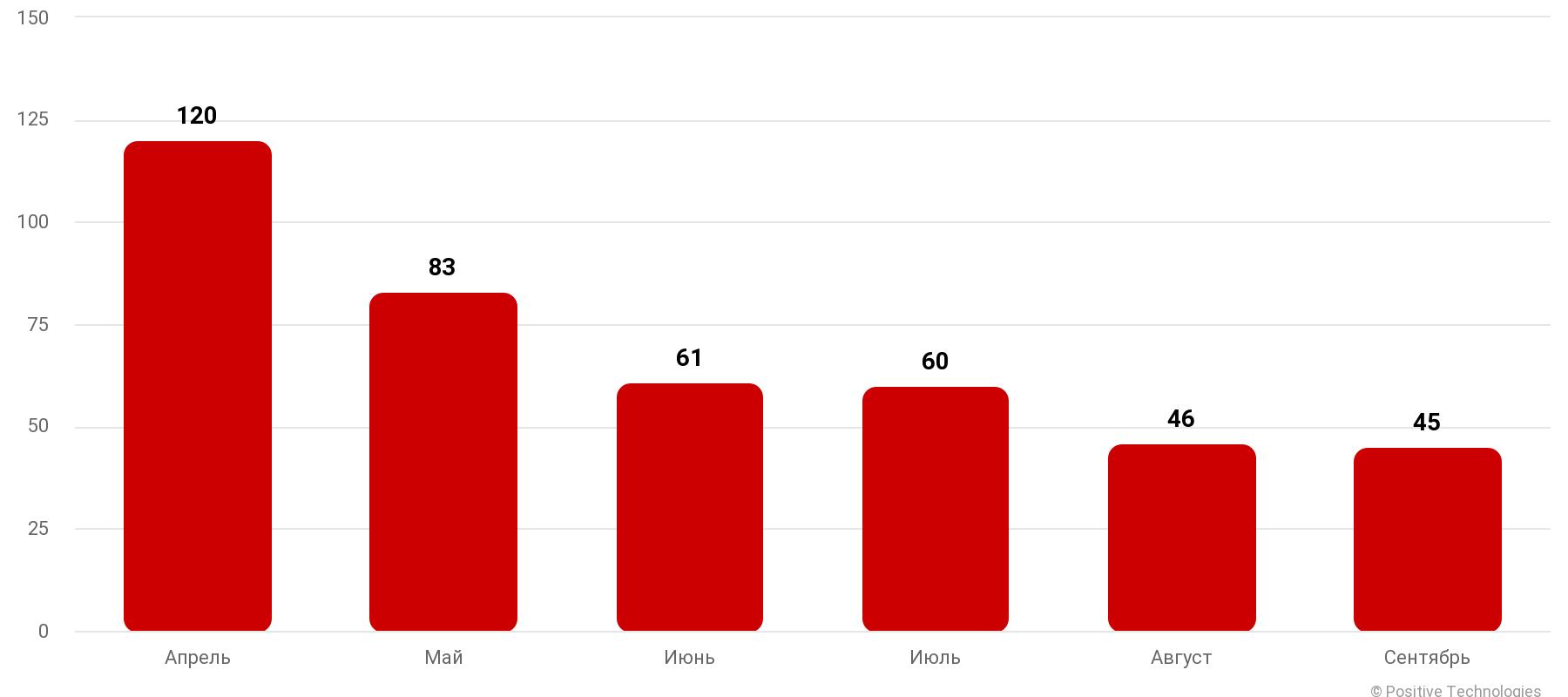
Number of ransomware attacks
According to the researchers, with an overall decrease in the share of attacks using malware against organizations (by 22 pp), cybercriminals’ desire to obtain data has led to an increase in the use of malware for remote control – from 17% to 36% in attacks against organizations, and for individuals, these malware already accounted for more than half of all used malware. Compared to the first quarter, in the third quarter of this year, the share of using malware for remote control in attacks against users increased 2.5 times.
In addition, according to the report, the share of attacks by APT groups increased to 5% of the total. According to experts, this is due to the launch of numerous phishing and intelligence campaigns against employees of various government agencies, industrial enterprises, and representatives of the press.
Compared to the same period last year, the share of attacks on individuals using social engineering methods increased from 67% to 83%. At the same time, attackers do not stand still and are constantly improving methods of deception, for example, forcing the victim to call a fake call center herself, as in the case of the BazaCall ransomware distribution campaign.
Using malware for remote control and downloaders in attacks against individuals.
Recall, by the way, that we wrote that FBI seized $ 2.3 million in cryptocurrency from partner of hack groups REvil and GandCrab.





