WordPress developers forcibly update Jetpack plugin on 5 million sites
Automattic, the company behind the WordPress CMS, has forcibly updated the popular Jetpack plugin on the 5,000,000 sites it is installed on.
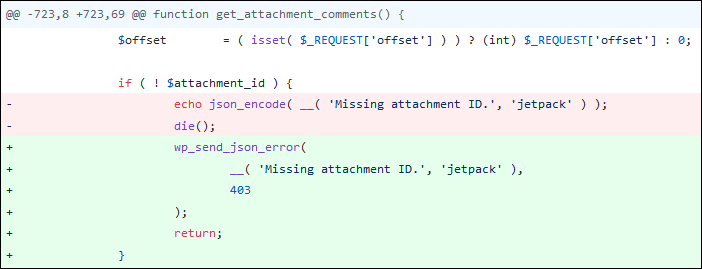
Jetpack provides its users with free features for security, performance and site management, including brute force attack protection, backups, secure login and malware scanning. The plugin is created and maintained by Automattic itself, which also develops WordPress.Jetpack recently found a vulnerability hiding in the Carousel function, thanks to which it is possible to display comments for each image.
No details about this bug have been reported yet, but it is known that Automattic has solved the problem by changing the authorization logic.
The company said in a statement that the bug affects all versions of the plugin since Jetpack 2.0, released in November 2012. Jetpack developers add that they are not aware of the exploitation of this problem by hackers in real attacks.
Since the specialists have prepared and force-distribute patches for all versions of the plugin since version 2.0, the download statistics available on WordPress Plugins now confirm that most installations have already received updates.
This is not the first time Automattic has released mandatory security updates to fix plugins or the CMS itself.
WordPress core developer Samuel Wood has previously said that the feature has been used “many times”, although he did not elaborate on the details. In 2015, another WordPress developer stated that the Force Plugin Update feature has only been used five times since its introduction in 2013.
Let me remind you that we wrote that Hackers exploit vulnerability in Easy WP SMTP WordPress plugin to reset admin passwords, as well as that Hackers compete for vulnerable WordPress sites.