Social Warfare allows WordPress site owners to add social network buttons to their resources, designed to share content from other sites.
Social Warfare is installed on 70,000 sites, and downloaded more than 805,000 times. According to the Wordfence team, the latest version of the plugin (3.5.2) contains a cross-site scripting vulnerability (XSS). Worse, researchers have noticed real attacks on sites where attackers exploit this flaw.
“Vulnerability allows attackers to inject malicious JavaScript code into links intended for sharing the material,” said Mikey Vinstra from Wordfence.
The attacks began after an unknown expert published a complete analysis of the gaps. That is why the plugin has been removed from the official repository.
On the Social_Warfare page, the WordPress team noted:
“The plugin was withdrawn on March 21, 2019. It is no longer available for download.”
The Social_Warfare team wrote on Twitter that developers are aware of the vulnerability, and is currently working on a patch that will be available to users soon:
Zero-Day Vulnerability Details
The plugin features functionality that allows users to clone its settings from another site. However, this functionality was not restricted to administrators or even logged-in users. An attacker is able to input a URL pointing to a crafted configuration document, which overwrites the plugin’s settings on the victim’s site.
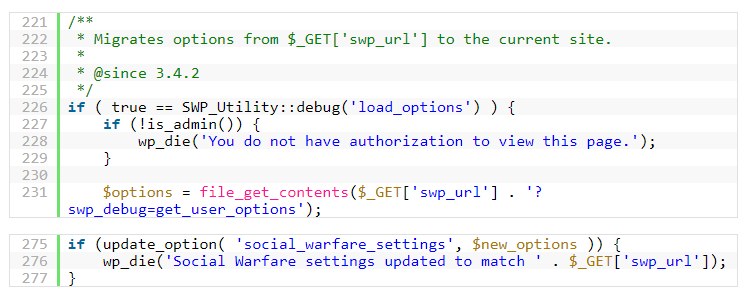
With the ability to modify the social media plugin’s settings, an attacker can pivot and perform more malicious activity. In all cases we’ve tracked so far, attackers modify the twitter_id value, as it most directly leads to a front-facing XSS injection point.