Play Ransomware Operators Could Have Accessed Swiss Government Data
The Swiss government has reported that in a recent Play ransomware attack on IT vendor Xplain, attackers may have gained access to their operational data. In addition, later the country’s authorities warned that they were the target of a powerful DDoS attack.
Let me remind you that we also wrote that Russian hackers intended to shut down Ukrainian electrical substations using Industroyer2 malware, and also that Russian Hackers Launched a Massive Spear-Phishing Campaign.And also information security experts said that the Russian DDOSIA Project Pays Volunteers to Participate in DDOS Attacks on Western Companies.
Last week, the Swiss government announced that it was affected by an attack on Xplain, a vendor that provides various government departments, administrative divisions and even the country’s armed forces with software solutions.
On May 23, 2023, Xplain was hacked by the extortionate group Play, and the attackers immediately stated that they had stolen various documents from the company containing personal and confidential data, financial and tax information, and so on. On June 1, 2023, the group published a full dump of the stolen data on their dark web site, as they apparently could not force Xplain to pay the ransom.
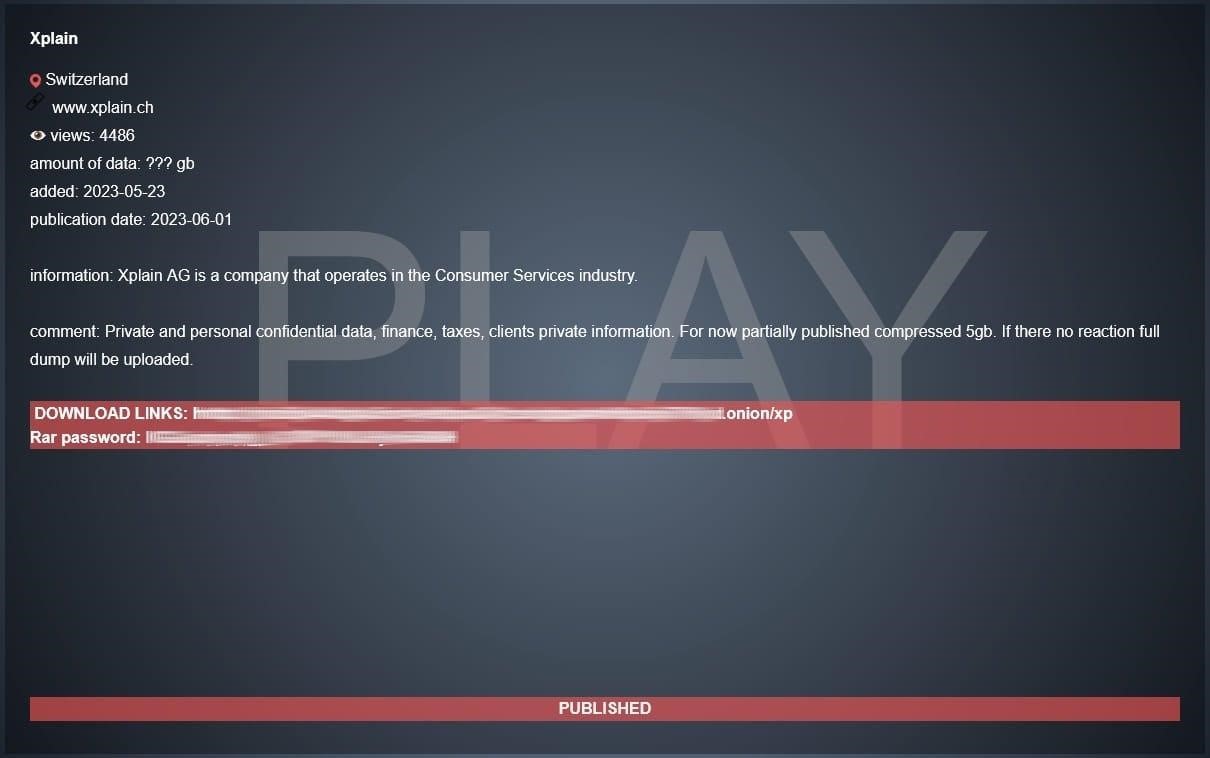
Play is leaking stolen data
Swiss authorities have now said that although the investigation into the incident is still ongoing, it is likely that the attackers leaked information belonging to the Swiss Federal Council into the public domain.





