Researchers measured the speed of ransomware
Splunk analysts conducted over 400 tests and measured the speed of various ransomware to determine how fast they encode files and assess the ability to respond to such attacks in a timely manner.
The researchers tested the speed of the 10 most common malware families by selecting 10 samples for each family (Avaddon, Babuk, BlackMatter, Conti, DarkSide, LockBit, Maze, Mespinoza, REvil and Ryuk).The malware was forced to encrypt about 100,000 files with a total size of about 54 GB. The files were stored on four hosts – two running Windows 10 and two running Windows Server 2019. In addition to encryption speed and duration, the researchers also studied how the ransomware uses system resources.
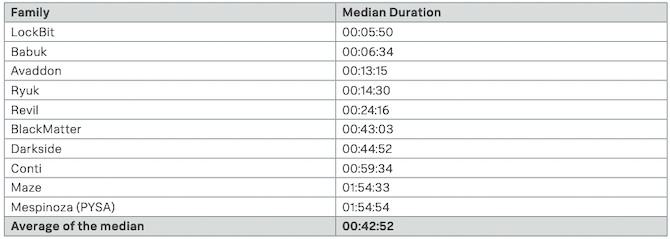
The researchers measured the time it took each malware to encrypt 100,000 files and used the average to calculate the speed of each malware family. The results showed that LockBit was the fastest at 5 minutes 50 seconds (over 25,000 files per minute), followed by Babuk at 6 minutes 34 seconds. The Conti malware encrypted files in just under an hour, while Maze and Mespinoza were the slowest: their result was almost two hours. The average data encryption time is 42 minutes and 52 seconds.
The analysis also showed that only some malware uses hardware to speed up the encryption process. The amount of device memory does not appear to have a significant impact on this process, but the speed of the work disk can speed up encryption, although this is most likely if malware can take full advantage of the CPU.
Let me remind you that we also reported that NetWalker ransomware operator sentenced to seven years in prison, and also that Trickbot ransomware wanted to open offices in St. Petersburg.





