SocGholish Malware Compromised and Infected Hundreds of News Sites in the US
Proofpoint experts have discovered a massive problem on American news sites — the malware called SocGholish attacks the media.
Let me remind you that, by the way, we wrote that Researchers Found That the Media Industry Is Most Vulnerable to Cyberattacks.
The attackers use the compromised infrastructure of an unnamed media company to deploy the malicious JavaScript framework SocGholish (also known as FakeUpdates) on media sites, the researchers said.
The publication Bleeping Computer, with which the researchers shared their findings, writes that experts track down the hacker group behind these attacks under the identifier TA569.
Hackers injected malicious code into a harmless JavaScript file that is uploaded to news sites. This file is then used to install SocGholish, which infects visitors to compromised sites with various malware, usually disguised as fake browser updates distributed as ZIP archives (for example, Chrome.Urdate.zip, Chrome.Updater.zip, Firefox.Urdate.zip, Opera .Update.zip, Oper.Updte.zip).
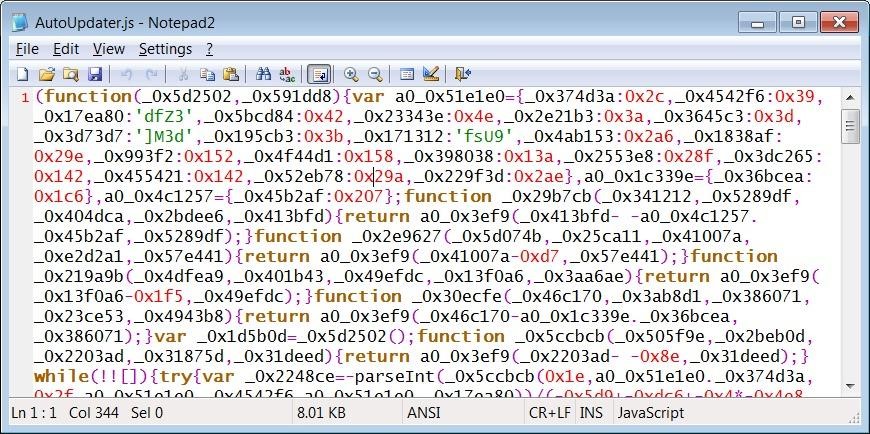
Obfuscated Malicious JavaScript
According to analysts, in total, malware was installed on the websites of more than 250 US news agencies, some of which are large and well-known organizations (the names of the affected resources were not disclosed). Although the total number of media outlets affected is not known, Proofpoint says that among the victims of this campaign are leading publications from New York, Boston, Chicago, Miami, Washington and so on.
The researchers say that the TA569 group has previously used media to spread SocGholish, and this malware could eventually lead to subsequent infections, including ransomware attacks.
Previously, SocGholish was used by the notorious Russian-speaking group Evil Corp, and the malware campaign discovered in 2020 was very similar to the current one. Let me remind you that at that time more than 30 large companies in the United States were infected with malware, which was distributed through fake warnings about the need to update software, sent through dozens of compromised American newspaper websites. Machines infected in this way were later used as an entry point into corporate networks, where the attackers deployed the WastedLocker ransomware.





