The researcher equipped the Cisco firewall with a bug, spending only $200
FoxGuard researcher Monta Elkins equipped the Cisco firewall with a bug, the so-called “hardware bookmark,” without much expense and efforts.
More than a year has passed since Bloomberg published an article describing the hardware “bookmarks” that were allegedly found on Supermicro server boards and allowed Chinese hackers to compromise them.Since this equipment is used by large technical companies, including Apple and Amazon, a huge scandal erupted. Representatives of Amazon and Apple were quick to categorically refute Bloomberg’s statements, and even the NSA said it was a “false alarm.” As a result, this whole story was immediately awarded two Pwnie awards: as “the most overpowered bug” and “the largest epic fail”.
Although Bloomberg’s messages have not found any evidence, the possibility of creating such “bookmarks”, of course, cannot be completely discounted.
Read also: Famous hacker through vulnerability in vBulletin crushed into forums for sex workers
So, FoxGuard specialist Monta Elkins decided to demonstrate that it is not complicated, and he will present the results of his work at the CS3sthlm conference, at the end of this month.
In the meantime, the researcher demonstrated the results of his work to Wired.
To implement the bug in the Cisco firewall, Elkins needed a soldering station for $ 150, a microscope for $ 40, several chips for $ 2, all equipment he ordered online.

“It seems to us that all this is some kind of magic, but in fact it is not so difficult,” says Elkins. – Having demonstrated hardware to people, I want to make all this more realistic. This is not magic. This is possible. I could do it in my basement. And there are many people smarter than me who can do this from virtually nothing.”
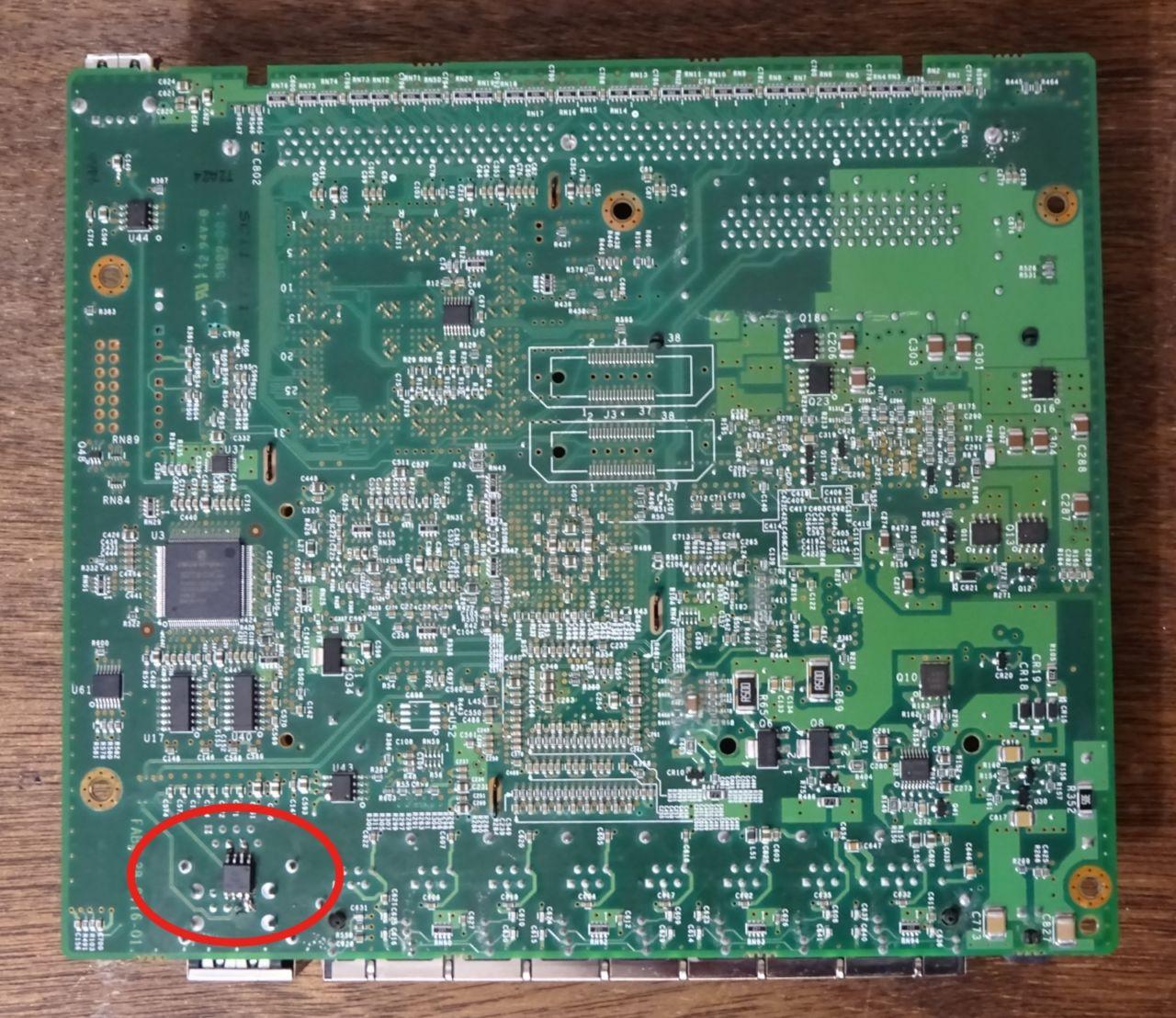
To create his “bookmark,” Elkins used the miniature ATtiny85 chip, which he found on the Digispark Arduino for $ 2. Having written his own code on the chip, Elkins removed it from the Digispark board and soldered it to the motherboard of the Cisco ASA 5505 firewall. To place the chip, he used an inconspicuous place that did not require additional contacts and allowed access to the COM port.
From the picture below you can understand how difficult it will be to notice such an “extra” chip on the board, even with the relatively small sizes of the ASA 5505 (6×7 inches). Elkins suggests that he could use an even smaller chip, but have chosen ATtiny85 to simplify the part of the experiment that involved programming.
Elkins programmed his bug to attack immediately after the firewall was placed and turned on in the target’s data center. The chip impersonates an administrator who accesses the firewall settings by connecting the computer directly to the port. Then the chip starts the firewall password recovery function, creates a new administrator account and gets access to the settings. After that, it is possible to change the firewall settings and provide attackers with remote access to the device.
Researcher explains that he used the Cisco ASA 5505 in his experiment because the firewall turned out to be the cheapest on eBay. But the attack should work against any Cisco firewall that offers password recovery in this way. Cisco experts have assured that they are already studying Elkins research and, if necessary, will take the necessary measures.
In essence, Elkins’ research continues another, earlier experiment, conducted by an independent information security expert, Trammell Hudson. Last year, during the Chaos Computer Conference, he demonstrated the Supermicro PoC board, on which the bookmarks of Chinese hackers were recreated, as they were described in the Bloomberg article. That is, a chip with access to BMC (baseboard management controller) was installed on the board.
At the same time, both experts emphasize that they did not try to confirm the story of Bloomberg about widespread attacks on the supply chain and do not even claim that such attacks are often found in reality.
“I want people to recognize that such implants are not a figment of someone’s imagination. They are relatively simple, says Elkins. “And if I can do this, it means someone with hundreds of millions of budgets has been doing this for some time.”