Bleeping Computer reports that a week ago RansomEXX ransomware attacked Konica Minolta. Many of the holding’s services suffered from the attack.
The first signs of a failure were noticed by the company’s customers back on July 30, 2020. Then users began to discover that the Konica Minolta product support site was down and displaying a temporary unavailable message.“The Konica Minolta MyKMBS customer portal is temporarily unavailable. We are working hard to resolve the issue and apologize for any inconvenience this may have caused you. If you need immediate assistance for service”, — said the message.
As a result, the company’s website was not working for almost a week, but the company did not answer questions about causes of the failure.
Worse, some Konica Minolta printers displayed a Service Notification Failed error, which forced the company to update their message and add a link to the documentation.
Although the company has yet to comment on the situation, Bleeping Computer reporters say their own source provided the publication with a ransom note proving Konica Minolta was the victim of a ransomware attack.
The file is called !!KONICA_MINOLTA_README!!.txt and a screenshot of this message can be seen below.
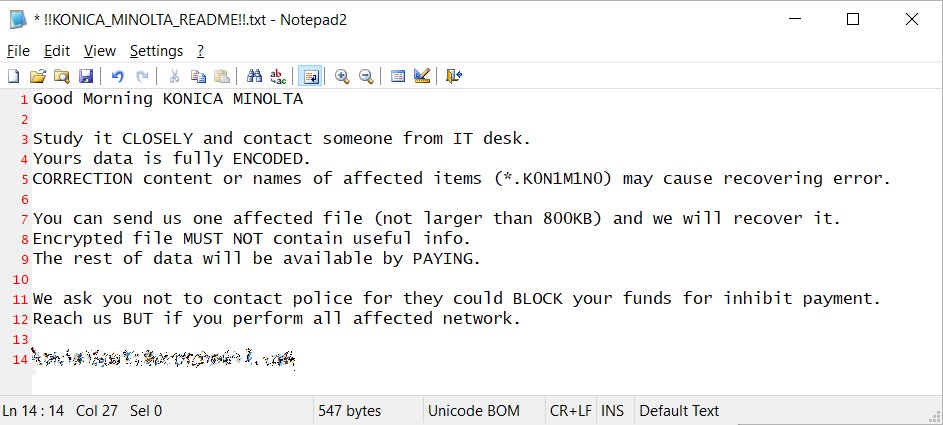
Also, journalists learned that the company’s devices were encrypted, and the extension of the affected files changed to .K0N1M1N0. The publication notes that the text of the note and the mentioned extension indicate that the company has become a victim of the RansomEXX ransomware.
RansomEXX was first detected in June 2020, when it was used to attack the Texas Department of Transportation. Like other similar ransomware targeting enterprises, RansomEXX is manually controlled. That is, first the attackers penetrate the network of the victim company, gradually spread the attack to various devices, and wait until they receive the administrator’s credentials. Then, through the domain controller, the attackers spread the malware to the entire corporate network at once, encrypting all files on all available devices.
According to Bleeping Computer, RansomEXX operators do not steal data from their victims before encrypting files, although many groups currently are doing this.
Recently, another tech giant, Canon, suffered from a ransomware attack, and we also wrote that MaxLinear chipmaker became a victim of Maze ransomware.





