Over 300,000 MikroTik routers are vulnerable to hacking
Researchers from Eclypsium stated that more than 300,000 routers of the Latvian company MikroTik are vulnerable to hacking by remote attacks. Because of them, devices can become members of botnets that steal confidential user data and participate in DDoS attacks.
Experts write that most of the vulnerable devices are located in China, Brazil, Russia, Italy and Indonesia.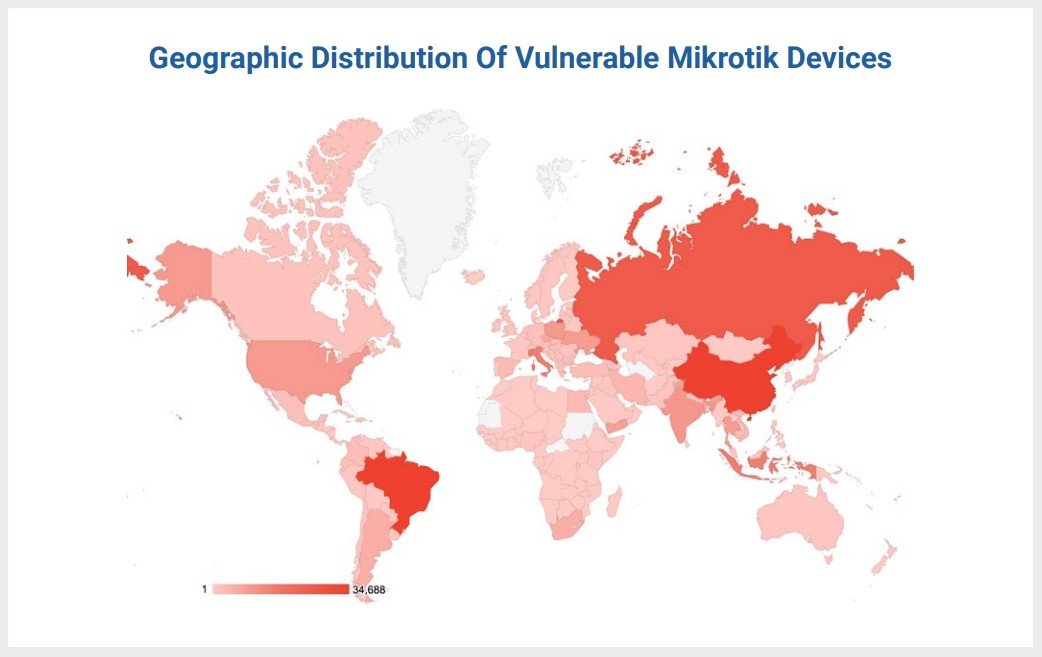
Researchers also remind that in the fall of this year, one of the most powerful DDoS attacks in history, perpetrated by the Mēris botnet, was also carried out using MikroTik devices.
The essence of the Eclypsium report boils down to the fact that administrators are often in no hurry to install patches for their MikroTik devices, which is why many of them are still vulnerable to dangerous remote attacks, although patches have been available for a long time. So, experts list the following vulnerabilities dated 2018 and 2019, which are often exploited by cybercriminals:
- CVE-2019-3977 (CVSS score: 7.5) – MikroTik RouterOS incorrectly validates the origin of service packs, thus resetting all usernames and passwords;
- CVE-2019-3978 (CVSS score: 7.5) – MikroTik RouterOS does not sufficiently protect a critical resource, which may lead to cache poisoning;
- CVE-2018-14847 (CVSS score: 9.1) – MikroTik RouterOS directory traversal vulnerability in WinBox interface;
- CVE-2018-7445 (CVSS Score: 9.8) – MikroTik RouterOS SMB Buffer Overflow Vulnerability.
After scanning the Internet, Eclypsium experts discovered about 300,000 MikroTik routers that are vulnerable to at least one of the vulnerabilities listed above. Also, experts say that they were able to identify about 20,000 unprotected MikroTik devices that injected mining scripts on all web pages visited by users.
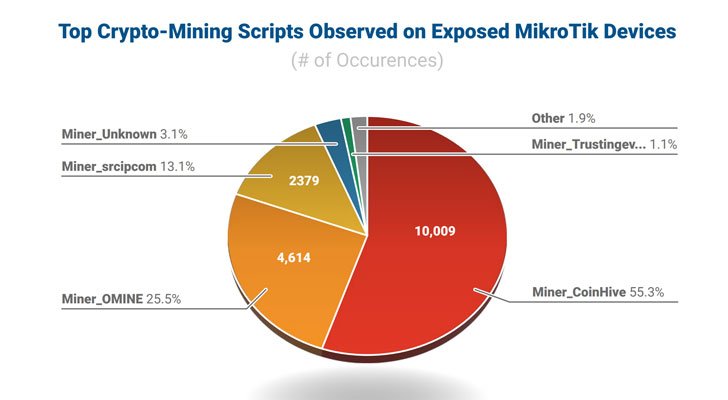
MikroTik representatives have already reacted to the publication of the report, and write that there are no vulnerabilities in the latest version of RouterOS, and router administrators should install updates and patches in a timely manner, and take precautions:
- do not open access to your device via the Internet for everyone;
- use strong passwords;
- do not trust the local network;
- block domains and endpoints associated with the Meris botnet;
- check the RouterOS configuration for unknown settings.
Recall that we also wrote that Microsoft Azure platform hit by 2.4 TB / sec DDoS attack also using the Mēris botnet.





