A team of Israeli information security experts spoke about the new DNS problem NXNSAttack, which allows enforcing power of DDoS attacks.
Researchers say the problem affects recursive DNS servers, as well as the DNS delegation process. Although NXNSAttack attacks can be implemented in different ways, the basic steps will be the same anyway:- An attacker sends a DNS query to a recursive DNS server. A request for a domain, such as attacker.com, is managed through an authoritative DNS server controlled by a hacker.
- Since the recursive DNS server is not authorized to resolve this domain, it will redirect the operation to the malicious DNS server of the attacker.
- A malicious DNS server responds to a recursive DNS server, stating that it delegates the DNS resolving operation to a long list of name servers. This list contains thousands of subdomains for the victim’s site.
- A recursive DNS server redirects a DNS query to all subdomains in this list, creating a huge load on the victim’s authoritative DNS server.
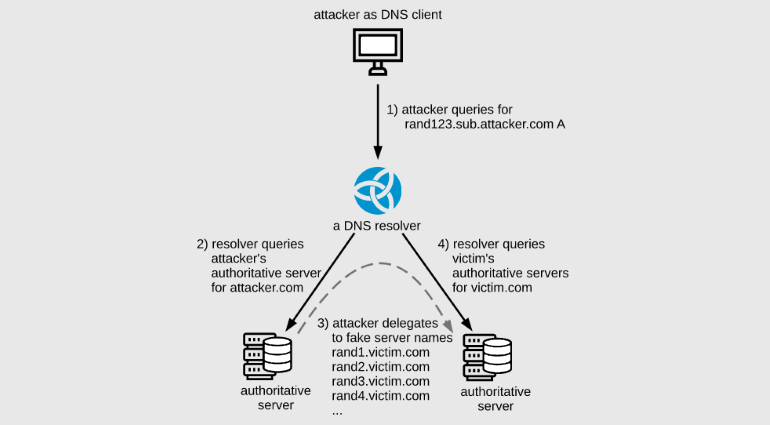
As a result, an attacker exploiting the NXNSAttack problem can amplify a simple DNS query by 2–1620 times compared to its original size. Such a load can lead to a failure of the victim’s DNS server, and when the DNS server shuts down, users will not be able to get to the attacked site, since the domain of the site cannot to resolve.
“The packet amplification factor will depend on the particular software running on the recursive DNS server, but in most cases the amplification will be many times greater than using other methods”, – write the experts.
According to the authors of NXNSAttack, currently such DDoS attacks are one of the most dangerous, because attackers can carry out lengthy and powerful campaigns by automating DNS queries and having only a few devices at their disposal.
To the NXNSAttack problem are vulnerable solutions such as ISC BIND (CVE-2020-8616), NLnet labs Unbound (CVE-2020-12662), PowerDNS (CVE-2020-10995), as well as CZ.NIC Resolver Knot (CVE-2020-) 12667) and commercial DNS services from large companies such as Cloudflare, Google, Amazon, Microsoft, Oracle (DYN), Verisign, IBM Quad9, and ICANN.
Over the past few months, experts have worked closely with DNS software vendors, content delivery networks, and DNS providers to secure DNS servers around the world from NXNSAttack.
Patches for NXNSAttack vulnerabilities have been actively released for several weeks, and they are designed to prevent abuse of the DNS delegation process. Administrators are advised to update their DNS resolver software to the latest version as soon as possible.
Recently, we said that the Google Play app launched DDoS attack on the ESET website, and at the same time China declared a real war on DDoS services.





