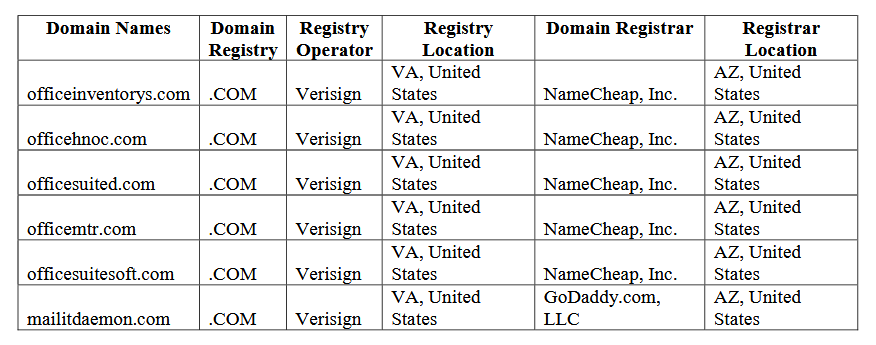
Microsoft through the court gained control over six domains of the so-called “Coronavirus” scammers. These domains have been involved in various phishing activities targeting Office 365 users.
Criminals have been active since December 2019 and have recently been actively exploiting the topics of the pandemic and COVID-19.Let me remind you that criminals attack even developers of COVID-19 vaccine during a pandemic.
Phishers sent emails to companies that hosted mail servers and corporate infrastructure in the Microsoft Office 365 cloud.
The emails were written as if they were written by a colleague or a trusted business partner of the victim.
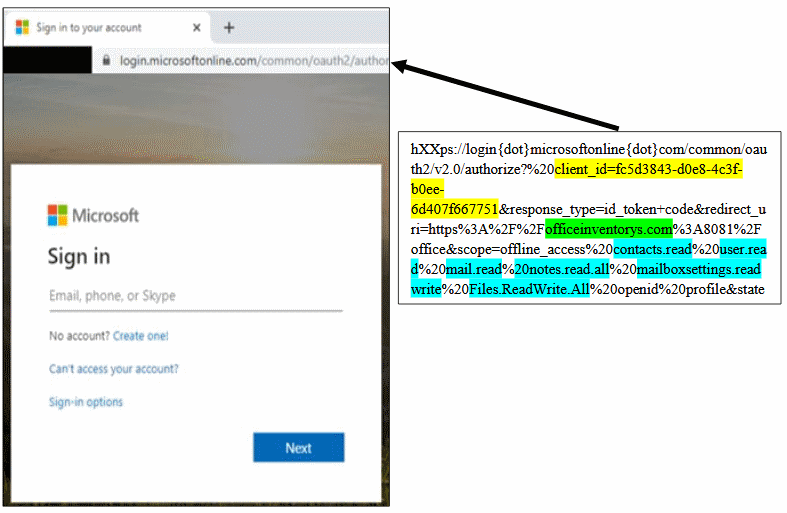
It is noted that this campaign was very unusual, since the attackers did not redirect users to phishing sites that mimic the login page in Office 365. Instead, hackers used an Office document. When users tried to open this file, a redirect was triggered to install a malicious third-party Office 365 application, created by cybercriminals.
If scammers caught the user and he installed the application, hackers got full access to his Office 365 account, settings, files, email content, contact lists, notes, and so on.
“Thanks to this application, hackers got full access to user accounts, even without password theft, because instead the attackers had the OAuth2 token”, – reports Microsoft.
Unfortunately, for a number of reasons, this fraud has been very successful. The fact is that the malicious application looked like an official and real one, as if Microsoft had really developed it.
In addition, the Office 365 environment is modular, and users are used to installing applications on a regular basis. Moreover, a link to install a malicious application firstly led users to the official Microsoft login page. Only after successful authentication, attackers made a trick and redirected victims to download a malicious application, creating the impression that the victims were using legitimate software, verified by Microsoft.
Researchers believe that at least two people were behind this campaign.
At first, phishers exploited topics related to business, but soon after the pandemic began, they turned to bait letters, supposedly containing documents on the coronavirus.
“Worse, third-party malware could be used to analyze the internal infrastructure of the victims, and then the attackers used the information gathered in this way for BEC attacks”, — said Tom Burt, Vice President of Microsoft Corporation.
Usually BEC (Bussiness Email Compromise) means compromised the legitimate email account of one of the employees of the company. After that, the attackers use this account to send fake letters to employees of the same company or its partners, and use social engineering to convince them to transfer funds to false accounts, hiding behind false invoices and fictitious transactions.
Let me remind you that in a similar way attackers cheated large companies, and there are also cases where deepfake’s were used to simulate CEO’s voice.





