Iranian hackers disguised themselves as an aerobics instructor
Proofpoint experts spoke about the activity of the hack group TA456, also known as Tortoiseshell and Imperial Kitten – for example, Iranian hackers masked themselves as a pretty athlete.
For more than 18 months, hackers pretended to be an aerobics instructor on Facebook and tried to trick the machines of employees of contractor companies working in the US aerospace defense (especially those involved in operations in the Middle East).The researchers write that for their targeted attack back in 2019, hackers created a Facebook and Instagram profile of a Marcella Flores, who was allegedly an aerobics instructor.
Moreover, Flores was just one of the many fictitious personalities that belonged to the group. The hackers took their time and spent months establishing contact with their targets, correspondence with them by mail and in private messages, before moving on to attempts to infiltrate malware.
It wasn’t until early 2021 that cybercriminals used a Gmail account owned by the defunct Flores to attack. From this mailbox, as part of a long-standing correspondence, hackers sent victims links to OneDrive, which led to a document with a diet survey or video file. The decoy was used to distribute an updated version of the Lideric malware, which the researchers call Lempo.
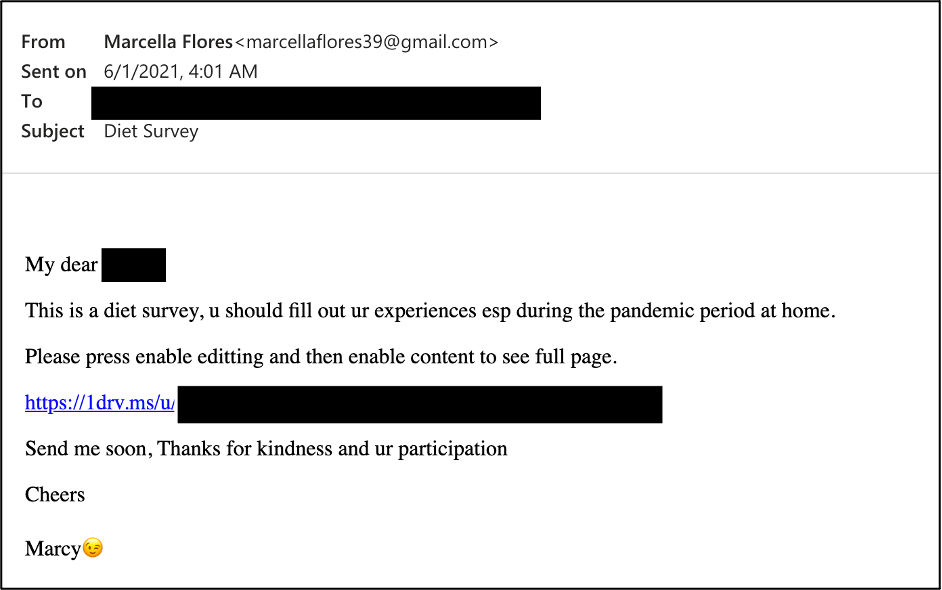
Lempo secretly locks onto the victim’s system, allowing attackers to search and steal sensitive information, including usernames and passwords. Proofpoint regretfully admits that it is impossible to say for sure whether these attacks were successful.
In theory, stolen credentials could help attackers develop attacks and spyware campaigns further. Stealing data from defense contractors could give hackers the ability to move further along the supply chain and gain access to the networks of defense and aerospace companies.
The profile of Marcella Flores is currently deactivated, and earlier this month Facebook announced the elimination of a sophisticated cyber-espionage campaign backed by Iranian group Tortoiseshell. According to the social networking site, the campaign targeted 200 military and defense and aerospace companies in the US, UK and Europe, and hackers used a “vast network” of fake online identities to attack.
Attackers often use publicly available target information to gain insight into their role, relationships, access to information, and attack vulnerabilities. Excessive dissemination of information on social media is a particularly risky behavior in such sensitive industries, so organizations need to make sure that their employees receive appropriate and regular security training,conclude the Proofpoint experts.
By the way, just in case, let me remind you that Famous hacker through vulnerability in vBulletin crushed into forums for sex workers.





