Trustwave recently reported that an unnamed Chinese bank forced Western companies to install official tax software containing the GoldenSpy backdoor. Now there is information that they detected another backdoor in the Chinese tax software.
The suspicious program was called Intelligent Tax and was developed by Golden Tax, a division of Aisino Corporation, specifically for local taxes.Soon after the publication of the expert report, it became known that the GoldenSpy backdoor was quietly removed from the program. At the same time Chinese developers secretly released uninstaller for GoldenSpy backdoor.
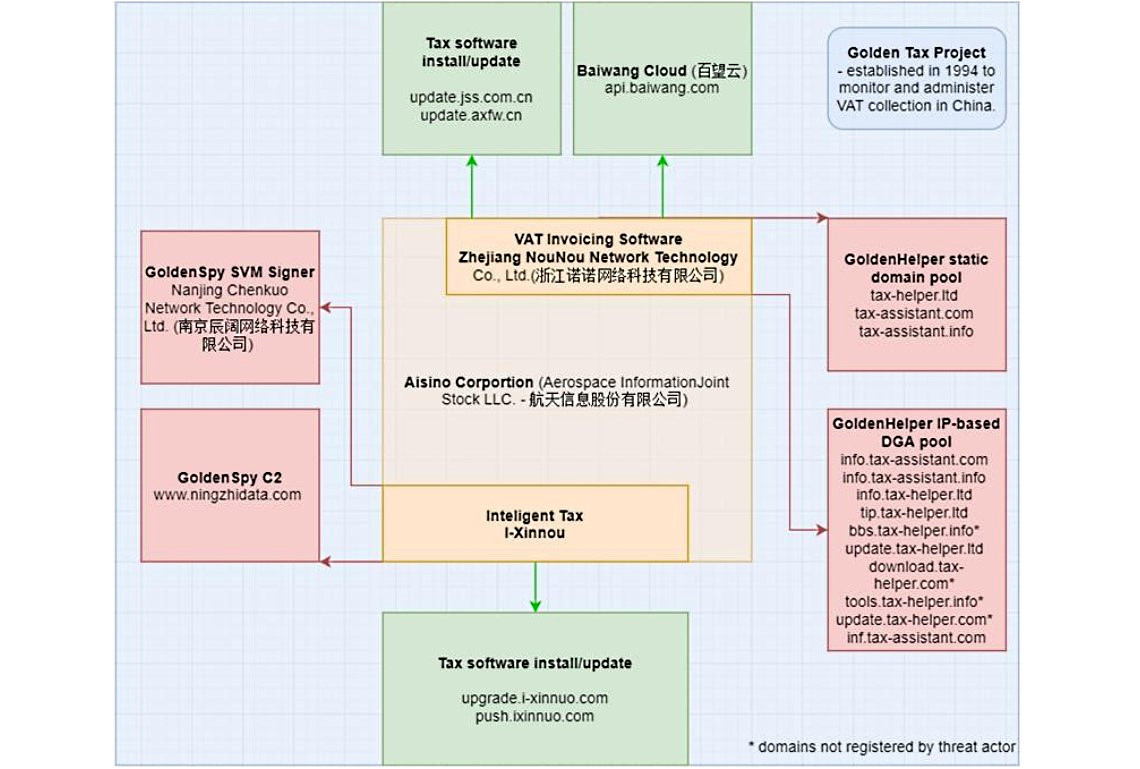
Now Trustwave experts say that GoldenSpy was not the first. So, the researchers found that another tax software, Golden Tax Invoicing Software (Baiwang Edition), hid the GoldenHelper malware. Companies registered in China are required to install this program because it is necessary for invoicing and paying value added taxes (VAT).
This software was also associated with a division of Aisino Corporation: GoldenHelper was digitally signed using a trusted certificate issued by NouNou Technologies, a subsidiary of Aisino Corporation. However, there are currently only two official tax program providers in China: Aisino and Baiwang. And the GoldenHelper malicious code was detected in the Baiwang authorship program.
Sometimes mentioned the programs were installed separately, but some users stated that a (hidden) copy of GoldenHelper was immediately installed in their version of Windows 7 Home Edition.
“Overall, GoldenHelper is similar to GoldenSpy and also represents a dangerous backdoor. So, it can be installed into the system without the consent of the user, increase privileges to the SYSTEM level, and then download and install additional payloads on the infected machine”, — say Trustwave analysts.
At the same time, the malware circumvents the User Account Control protection mechanism in Windows, which usually asks the user to issue permissions to specific software to install other programs and make changes to the system.
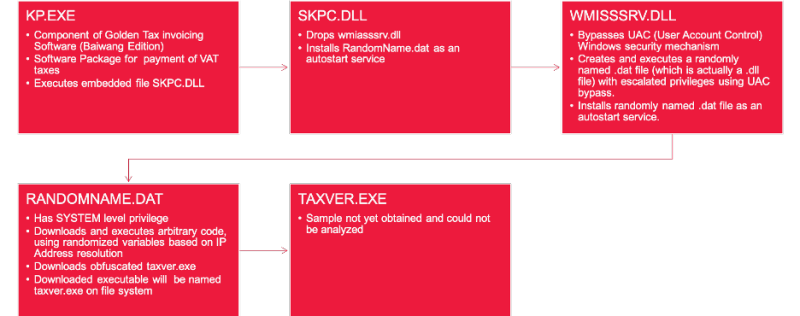
Experts say that GoldenHelper uses SKPC.DLL to interact with Golden Tax, WMISSSRV.DLL to elevate privileges and a .DAT file with a random name to select and run arbitrary code with SYSTEM privileges. The main goal of this malware is to download and run taxver.exe, but experts could not find the actual sample of this payload.
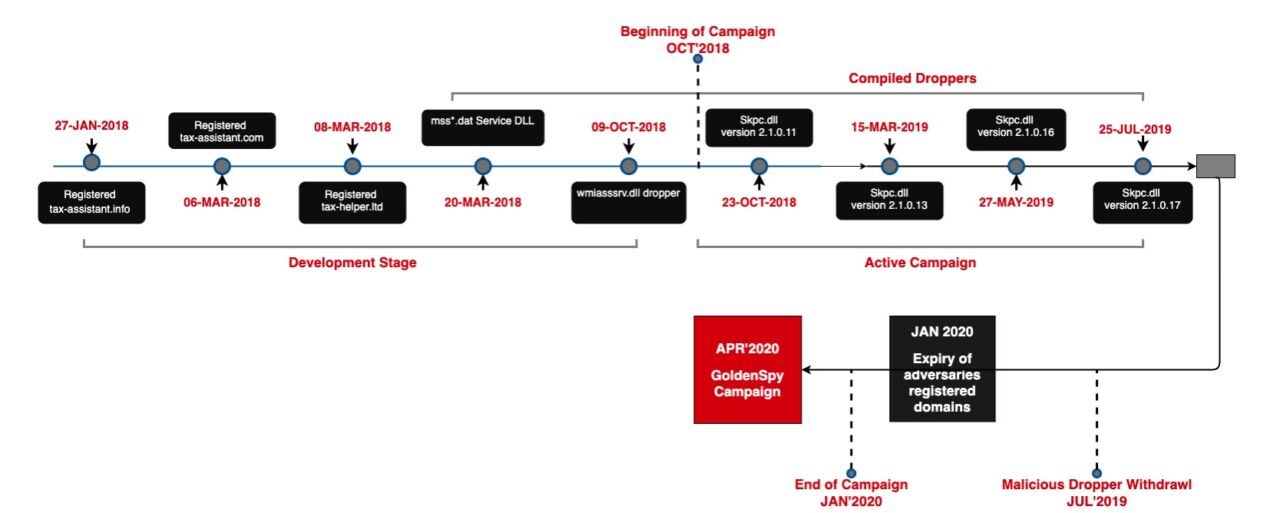
The fact is that the GoldenHelper campaign was active in 2018-2019, and now, it seems that it has already ended. The frequency of detecting images of malware, involved in this campaign increased in mid-2019, and this, apparently, forced hackers to curtail the operation, and the domains of the control servers expired in early 2020.
In general, GoldenHelper was able to:
- Use randomly generated file names;
- generate random timestamps creation and last write;
- Download executable files using fake file names with the extensions .gif, .jpg and .zip;
- Use IP-based DGAs to change the address of the management server on the fly.
Although the researchers were unable to prove that taxver.exe is really bad news, they note that legitimate software usually does not bypass Windows security tools to increase privileges, does not randomize its location, does not hide its name, does not try to make changes to DNS records, and so on. Further.
Trustwave experts conclude that GoldenHelper was obviously the predecessor of GoldenSpy:
“GoldenSpy followed the GoldenHelper campaign, and we have no doubt that this threat will continue to evolve into a new methodology aimed at enterprises operating in China.”