Microsoft fixes 0-day NTFS corruption bug
In January 2021, users and the media noticed that an unpatched 0-day bug in Windows 10 (and older OS versions, including Windows XP) allows corrupting the NTFS file system structure with a one-line command.
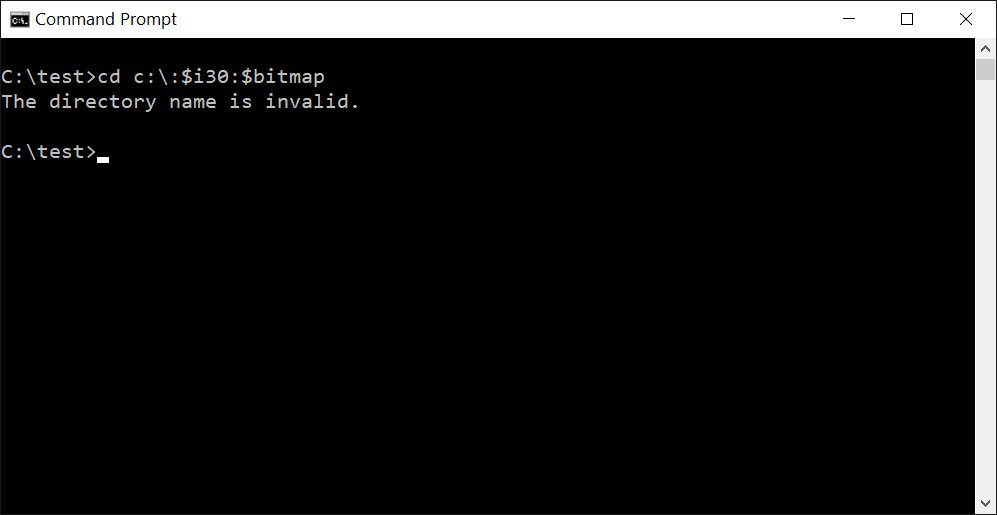
The problem was discovered last year by cybersecurity researcher Jonas Likkegaard. In August and October 2020, he already tried to draw attention to this bug, but achieved success only in 2021.A bug and NTFS corruption can be triggered by simply trying to access the NTFS $ i30 attribute in a specific way. Below you can see an example of such a dangerous one-line command. Warning: do not test the bug on your own running system, rather use a virtual machine for this!
An exploit for this problem could be hidden inside a shortcut file, ZIP archive, batch files, and so on, and such files caused immediate damage to the file system structure.
While Microsoft engineers explained that the drive was not actually damaged and chkdsk would successfully fix the problem, some users reported that chkdsk didn’t work for them, and Windows 10 still refused to boot.
It was supposed that a fix for this error would appear in February, but this did not happen. Then the Mozilla developers added a special check to Firefox 85.0.1 to prevent access to the problematic path, and the OSR specialists prepared an unofficial open source patch for this error.
“OSR, a software development company specializing in Windows internals, has released an open-source filter driver that prevents the NTFS bug from being abused while waiting for an official fix from Microsoft”, — reported Bleeping Computer journalists.
Now, a fix has finally been added to Windows 10 Insider Build 21322 that prevents access to the problematic path. If user tries to run the above command, the system will respond with “Invalid directory name” and will no longer mark the drive as damaged.
But, unfortunately, so far the patch can be applied only for Windows 10 Insider “Dev”, but not Windows 10 21H1 “Beta”, which is due out this spring.