Malwarebytes experts talked about an interesting MageCart campaign, for which hackers created a website to host favicon and mask malicious code as favicon.
Let me remind you that initially the name MageCart was assigned to one hack group, which first began to use the so-called web skimmers on websites to steal bank card data.“Hackers hack sites and then inject malicious code into their page that records and steals payment card data when users enter it during checkout”, – write Malwarebytes researchers.
This approach turned out to be so successful – the MageCart script was even inbuilt into the Forbes subscription site, the group soon got numerous imitators, and the name MageCart became a common noun, and now embraces a whole class of such attacks.
And if in 2018 RiskIQ researchers identified 12 such groups,by the end of 2019, according to IBM, there were already about 40 of them. And Europol put MageCart in the list of the most dangerous cyber threats of 2019.
Researchers at Malwarebytes write that the hack group brought their operations to a whole new level of complexity. The company’s analysts revealed a malicious campaign, investigating a series of strange hacks, the sole purpose of which was to substitute favicon on hacked sites.
![]()
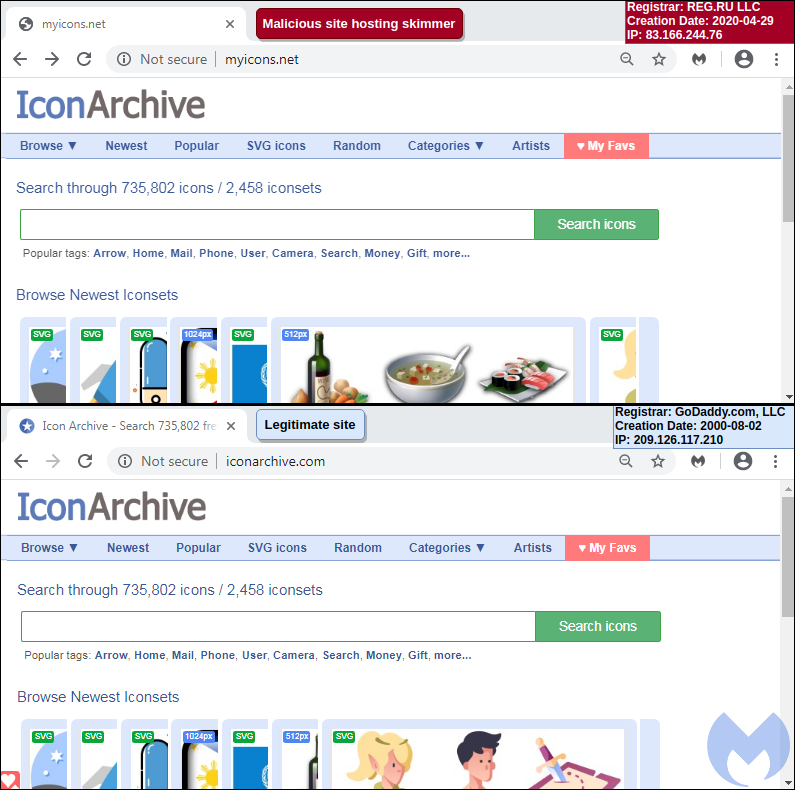
The new favicon were image files hosted on MyIcons.net and did not contain malicious code. Although at first glance this substitution looked completely innocent, experts found web-skimmers on all the affected sites, and something was wrong with the new favicon.
As further investigation showed, the trick was that the MyIcons.net site provided a legitimate favicon file for all pages of the attacked resource, except for those where were placed the order forms.
“On the checkout pages, MyIcons.net replaced the usual favicon with a malicious JavaScript file that created a fake payment form and stole user card details entered into it”, – report Malwarebytes experts.
Experts note that site owners, which noticed calls to MyIcons.net, would find a harmless favicon hosting portal. However, in fact, this site was a clone of the legitimate portal IconArchive.com and served as a regular screen for attacks.
In addition, it is worth noting that this site was hosted on the same servers that were previously used in other skimmer operations, which noticed a few weeks ago Sucuri specialists.





