Hackers exploit vulnerability in Easy WP SMTP WordPress plugin to reset admin passwords
Last week, the popular Easy WP SMTP plugin for WordPress, installed more than 500,000 sites, was patched for a serious administrator password reset vulnerability.
This plugin allows site owners to configure SMTP settings for outgoing emails from their site.According to researchers from Ninja Technologies Network, Easy WP SMTP version 1.4.2 and later versions contain a feature that generates debug logs for all emails sent by a site, which are then saved in the installation folder.
“The Easy WP SMTP plugin has an optional debug log where it writes all email messages (headers and body) sent by the blog. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/”. The log is a text file with a random name, e.g., 5fcdb91308506_debug_log.txt”, – say Ninja Technologies Network experts.
And they also report that there is no index.html file in the plugin folder, and therefore, on servers where the directory listing is enabled, hackers can find and view this log.
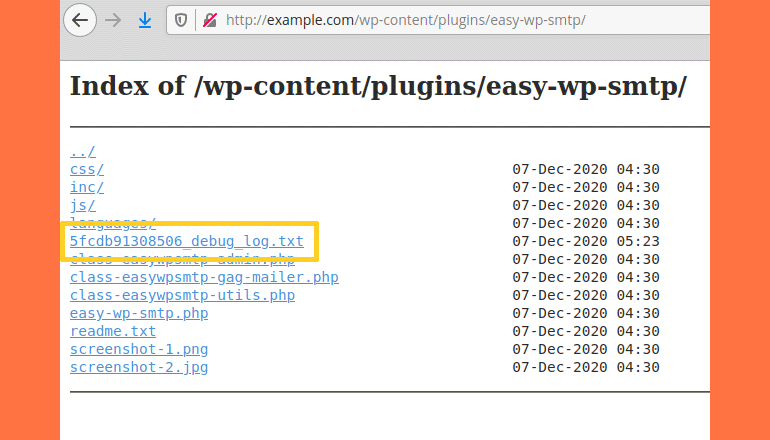
Experts warn that automated attacks have been directed at sites with vulnerable versions of the plugin for about two weeks, their purpose was to identify the administrator account and then initiate a password reset for it.
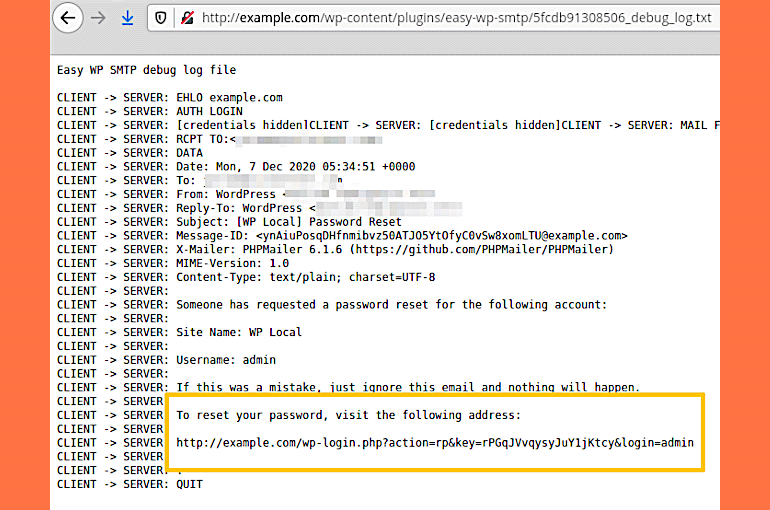
The fact is that for to reset the administrator password, attacker has to send an email with a special link, and this letter also ends up in the Easy WP SMTP logs. Basically, all an attacker needs to do is access the debug log, find the password reset link there, and hijack the site’s administrator account.
It should be noted that this is not the first critical bug in Easy WP SMTP. So, in 2019, a problem was discovered in the plugin that allowed third parties to enable user registration and then create new administrator accounts.
Let me remind you that we talked about the fact that hackers compete for vulnerable WordPress sites, and also that vulnerabilities in two plugins endanger a million of WordPress sites.
As mentioned above, the plugin developers have already fixed the vulnerability. The patch is included in Easy WP SMTP version 1.4.4.
Update immediately if you have version 1.4.2 or below installed.
Consider disabling the debug log, as it could lead to a leak of sensitive information (messages, passwords etc).





