Spyware Developers Ready to hack iOS and Android for 8 million euros
Documents from legal spyware company Intellexa (similar to NSO Group) have leaked online: according to these papers, the little-known company offers various services, including exploits for Android and iOS devices, which they promise to hack for 8,000,000 euros.
Exploit brokers, hired hackers, and legal spyware vendors have come into the spotlight of late, largely due to recent revelations about the use of the Pegasus spyware, developed by Israeli company NSO Group.Let me also remind you that we wrote that Attackers infected iPhones of American diplomats with NSO Group spyware.

One of NSO Group’s new competitors is Intellexa, founded by Israeli entrepreneur Tal Dilian. On its website, the company says it offers technology that is designed for law enforcement and intelligence agencies to “help protect the public.” Also, according to the site, Intellexa is based in the EU and has six own sites and R&D laboratories in Europe.
The other day, an information security specialist known under the pseudonym vx-undergroud (who often leaks malware source codes and other cybersecurity insiders) published a number of documents on Twitter that represent Intellexa’s commercial offer. The papers are not dated, but vx-undergroud writes that these screenshots were posted on the Russian-language XSS hack forum on July 14 of this year.
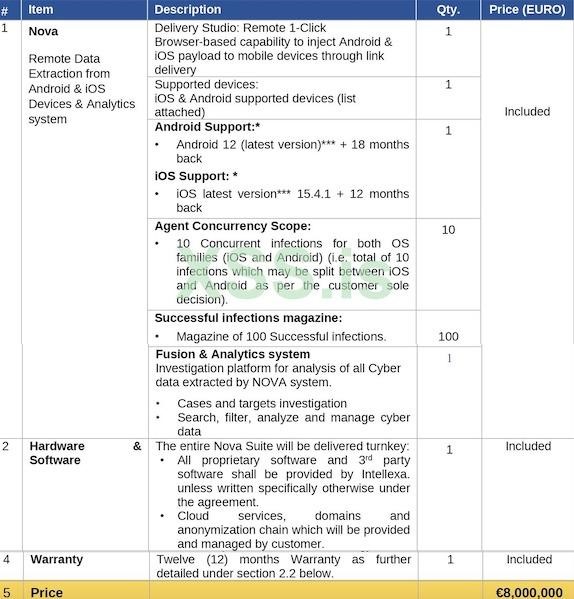
Documents marked as proprietary and confidential describe remote data retrieval services for Android and iOS devices. In particular, we are talking about remote browser-based one-click exploits that allow you to inject a payload on victims’ mobile devices based on Android or iOS. The short description says that to deliver the exploit, the target only needs to follow the link.
Additionally, in the documents users can see an incomplete list of Android devices against which such an attack will supposedly work.
The company says its exploits are up to date for iOS 15.4.1 and the latest Android 12. Since Apple released iOS 15.4.1 in March 2022, the documents appear to have been created very recently. Since then, three security updates have been released, which means that it is likely that Apple could already fix one or more 0-day vulnerabilities exploited by Intellexa. However, it is not uncommon for vulnerabilities exploited by such companies to remain unpatched for quite a long time.





