GoDaddy closed 15 000 subdomains that used spammers
GoDaddy turned offline 15 000 subdomains that were used in spamming campaigns.
In this campaign, intruders lured users on pages of websites that sale fake products.Traditionally, users received emails with advertisement of some product. If a victim opened a link from the letter, they got in one of subdomains that based on completely legitimate resource (without informing its owner).
These resources offered products, allegedly approved by celebrities as Steven Hocking, Jennifer Lopes, and Gwen Stephany, etc. In reality, these statements were not true.
Majority of advertised products were stimulators as cannabinoid oil, weight-losing pills and so on.
This spamming operation discovered Palo Alto Networks specialist Jeff White. For two years White traced criminals actions, collecting and analyzing information.
Jeff White reported:
“After speaking with some of our customers, hunting for various URLs, and reviewing quite a few other research blogs, I was able to put together a pretty clear chain of events”
- User clicks a link from spam e-mails, random/hijacked Skype messages, Facebook ads, and Twitter posts.
- User ends up on a redirection site, which were usually legitimate sites compromised in some way, which may involve a few hops.
- User ends up on a fake celebrity endorsement landing page.
- User ends up ultimately on a sales page for the product being sold.
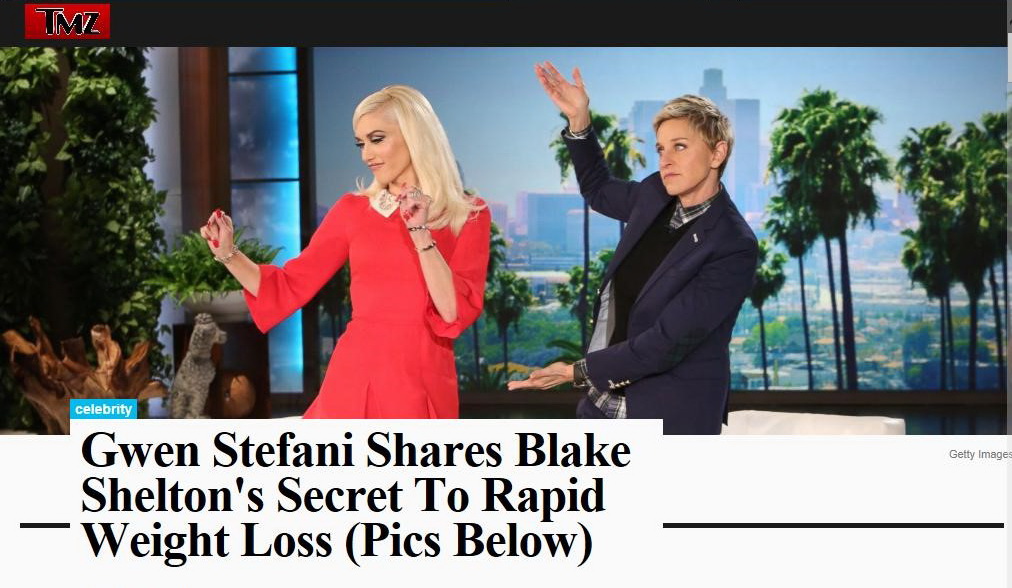
Gwen Stefani variant of spammer page
At the beginning of the year expect shared his materials with GoDaddy that was exploited by malware subdomains. GoDaddy representatives launched own investigation. It revealed that intruders used fishing for stealing clients credentials and opening access to their accounts. After obtaining access was created special subdomain where could be found described above products.
GoDaddy was decisive while addressing his issue – it not only turned offline all malware subdomains, but also restored credentials of involved clients





