In a new GitHub report, representatives of the web service talked about the problems of fixing some vulnerabilities. Based on a study of over 45,000 active repositories, the report demonstrates that it often takes developers years to fix vulnerabilities in their software.
So, it usually takes 7 years to fix vulnerabilities in Ruby, and it usually takes 5 years to fix vulnerabilities in npm. Such a long time frame is due to the fact that bugs often go unnoticed.“Vulnerabilities often go unnoticed for more than four years before being discovered. Once they are discovered, it is common for package maintainers and security specialists to create and release a fix in as little as four weeks”, — write the GitHub experts.
All repositories covered in this report use one of six package ecosystems (Composer, Maven, npm, NuGet, PyPI, or RubyGems) and have a dependency graph included. In open source environments, the most common dependencies are JavaScript(94%), Ruby(90%) and .NET(90%).
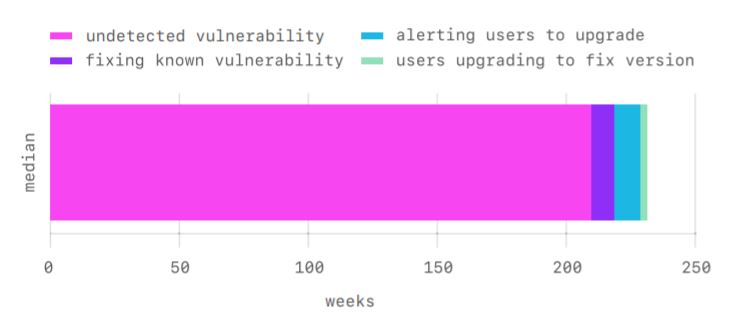
At the same time, according to statistics over the past 12 months, Ruby (81%) and JavaScript (73%) repositories had the highest chance of receiving a security warning from Dependabot.
By the way, we talked about a funny misunderstanding with the service itself when the GitHub source code has been uploaded to GitHub. The company denies the hack.
It is also noted that most of the vulnerabilities are the result of programming errors and have nothing to do with malicious attacks. In particular, an analysis of 521 alerts showed that only 17% of them were associated with any malicious behaviour.
“Security vulnerabilities can affect software directly or through its dependencies — any code that is referenced and associated with a software package. That is, the code may be vulnerable due to the fact that it itself contains vulnerabilities, or because it relies on dependencies that contain vulnerabilities”, — the report explains.
The report also notes that CVE-2020-8203 (Prototype Pollution in lodash, one of the most popular npm packages) can be considered the most serious vulnerability of the year, as it caused more than 5,000,000 Dependabot detections.
Let me remind you that GitHub imposes sanctions on accounts of developers from Iran, the Crimea and Syria.