Attackers can spy on you through certain models of D-Link cameras
IT-security experts advice to temporary refuse from usage of remote access function in D-Link DCS-2132L cameras that are set in important parts of house or office.
Reason for it is presence of vulnerabilities that enable video stream interception and devices’ firmware modification.ESET company experts noted security issues with D-Link DCS-2132L last year. The most dangerous of them creates all necessary conditions of performing “man-in-the-middle” attack.
“The most serious issue with the D-Link DCS-2132L cloud camera is the unencrypted transmission of the video stream. It runs unencrypted over both connections – between the camera and the cloud and between the cloud and the client-side viewer app – providing fertile ground for man-in-the-middle (MitM) attacks and allowing intruders to spy on victims’ video streams”, — report ESET researchers.
Attackers can restore and repeat video stream any time as well as receive current picture from the camera.
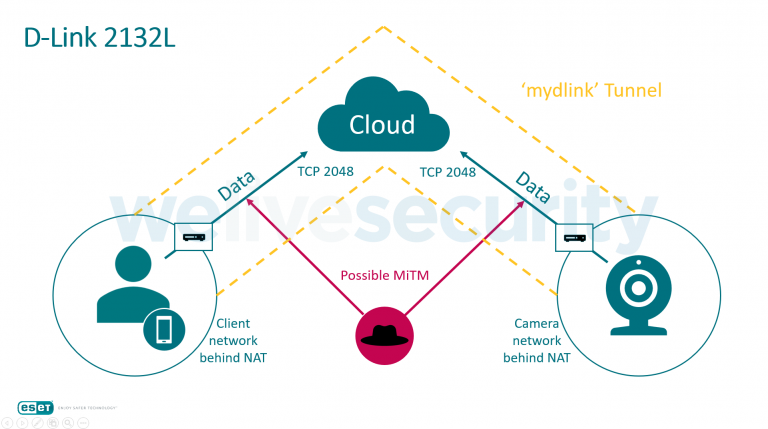
Scheme picturing the vulnerable data transmission and possible MitM attack vectors.
Second issue involves MyDlink plugin for browsers that allows users to watch streams without entering application. With the use of this vulnerability attacker can substitute legitimate device’s firmware by a malware one. However, this attack is difficult to perform.
Additional vulnerabilities were also found in the Universal Plug and Play set of protocols that uses camera. Universal Plug and Play opens port 80 on home routers, by this making HTTP-interface available for attackers that scan Internet searching for open ports.
Currently through Shodan service can be found about 1600 D-Link DCS-2132L cameras with open port 80, majority of them in US, Russia and Australia.
Producer launched set patches for some vulnerabilities, but it is still not complete.
As showed testing that conducted ESET researchers, vulnerability in MtyDlink service that fully eliminated, while other plugins are not fixed yet.
D-Link DCS-2132L camera is still available on the market. Current owners of the device are advised to check that port 80 isn’t exposed to the public internet and reconsider the use of remote access if the camera is monitoring highly sensitive areas of their household or company.
Source: https://www.welivesecurity.com





