How to avoid spam and phishing scams in email? Part 2
What is Spam – part two
You can read part one here.
Another politician, whose name is often flashed in spam – Donald Trump, one of the two contenders for the presidency in the United States. The unique technique of online earnings from the Trump, according to the promises spammers will enrich anyone who wants to learn more and follow the link from the message. Tellingly, the reports were issued as news outlets CNN and Fox News.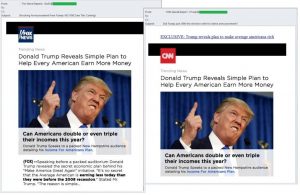
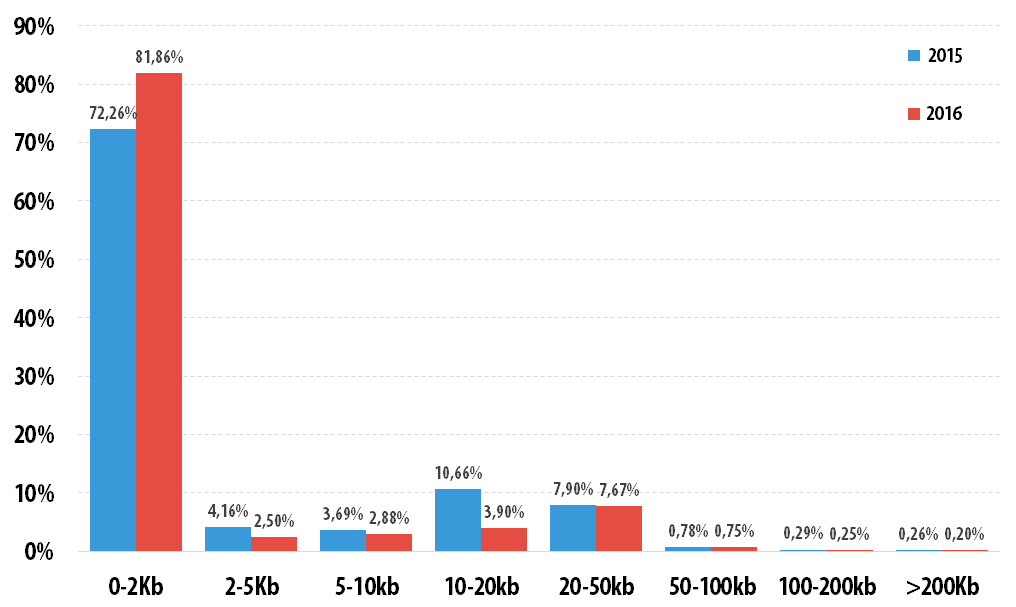
Often spam latters are now so big, so users download it really fast. Bellow you can see average statistic what will show you how big this spam latter can be. Traditionally, most send letters in the 2015 were reported up to 2 KB (72.26%), although their share fell by 9.6 percentage points In contrast, by 6.76 percentage points the share of letters from 10 to 20 KB. In the other categories the minimum changes.
The three leaders still a family of Trojan-Downloader.JS.Agent (10,45%), Trojan-Downloader.VBS.Agent (2,16%) and Trojan-Downloader.MSWord.Agent (1,82% ). Trojan.Win32.Bayrob family now occupies the 4th place (1.68%). Family Backdoor.Win32.Androm (0,55%), in contrast, has lost several positions, 4th to the penultimate line of the rating.
 The country with the highest proportion of people are attacked by phishers was China (20.22%). the proportion of the attacked people in this country is lots more than in other countries
The country with the highest proportion of people are attacked by phishers was China (20.22%). the proportion of the attacked people in this country is lots more than in other countries

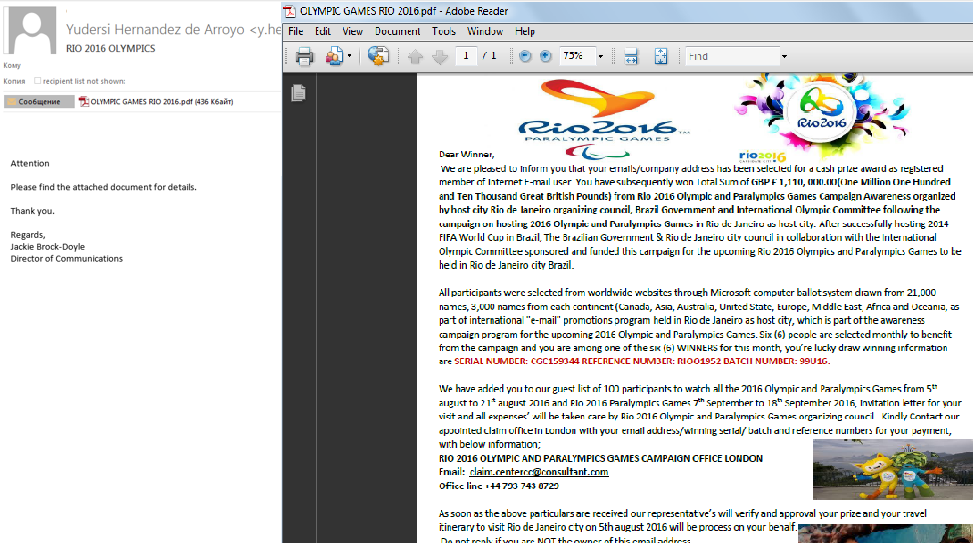
Brazil is not the first year is in the top countries with the highest proportion of people are attacked by phishers. Thus, in 2015 and 2016, the attention was drawn scams Olympics, which is being held in Brazil. In the last few month potential victims of phishing were not only ordinary people, but also the organizers of the Olympic Games.
Users of social networking site Facebook are often subjected to phishing attacks. During one of the attacks, the scammers have noted potential victims on the provocative video. To view it needed to go to a fake page, which was disguised as a popular YouTube video portal, and install a browser extension, what will redirect their browser to different adult sites and etc. This extension requested permission to read all data in the browser, potentially allowing scammers get saved passwords, logins, credit card details and other confidential user information. In addition, further expansion of the spread links to Facebook, but on behalf of the victim.
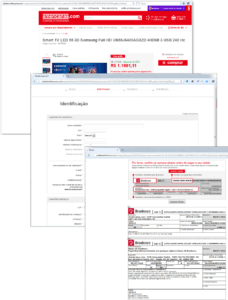
To bypass the security software filters phishing scammers trying to locate the page on reputable domains. So the probability of blocking is significantly reduced, and the confidence of potential victims grows. Big success for phishers – get domain for the purposes of a bank or government agency. Last well know phishing attack aimed at visitors to the popular Brazilian e-commerce site – a fake page is located on the domain of the large Indian bank. This is not the first time that fraudsters hack into the domain of a large bank and place it to your content. When user tries to buy anything on a fake page scammers requested a lot of personal information, so phishers get use it as they want. For further payment offered to print a check with logo of a Brazilian bank.
More often phishers trying to hack through state structures sites. So, there are a lot of cases when the phishing pages on the domains of public authorities of different countries. Here are some of them: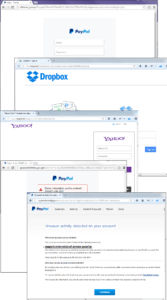
Hackers concentrated most of its force on the user’s most popular brands, thereby increasing the chances of success once a phishing attack. On the top 3 organizations attacked by the hackers for the last year was Mictosoft, “Global Internet portals” as with a single account, the user gets access to a variety of services. It attracts hackers – in the case of a successful attack to gain access to a variety of services used by the victim.

Conclusion
Among the countries – targets of malicious attachments leader for the quarter is Germany, followed by a small margin followed by China. Closes the top three of Japan, which in the first quarter ranked seventh.
The most common family of malicious programs in the mail remains Trojan-Downloader.JS.Agent, followed by Trojan-Downloader.VBS.Agent and Trojan-Downloader.MSWord.Agent. A significant amount of malicious spam was used to spread the Trojan ransomware, such as Locky. Interestingly, almost a month did not send his attackers malicious spam botnet Necurs but then again earned. In the near future don’t expect a significant reduction in the amount of malicious spam, though you can change the patterns of letters, the complexity of malware, as well as social methods by which attackers provoke a user to run malicious attachment.
The direction of phishing attacks has shifted a little bit from the theme “Global Internet portals” to the “Financial Institutions”.
Like phishing, and spam scams actively used the theme of the Olympic Games in Brazil. Criminals trying to lure users to a fake page and get their confidential information or just lure victims money.
The political events such as elections in the US, too, came to the attention of spammers.
In phishing, compromised sites used by public authorities.
As we can see, scammers obtaining money from users by a complex scenario, but rather a direct way, such as the download of Trojans cryptographers, forcing vulnerable users to pay a ransom, or phishing, aimed at financial institutions. All of this confirms that every user needs good protection to save their private information while they using the Internet.