Researcher Says Apple Downplayed the Danger of The Vulnerability He Found
Indian information security specialist Laxman Muthiyah claims to have discovered a critical vulnerability related to the password reset function on Apple devices, and the company has downplayed its danger. According to him, the bug could have been used to hijack any iCloud account, but Apple believes otherwise.
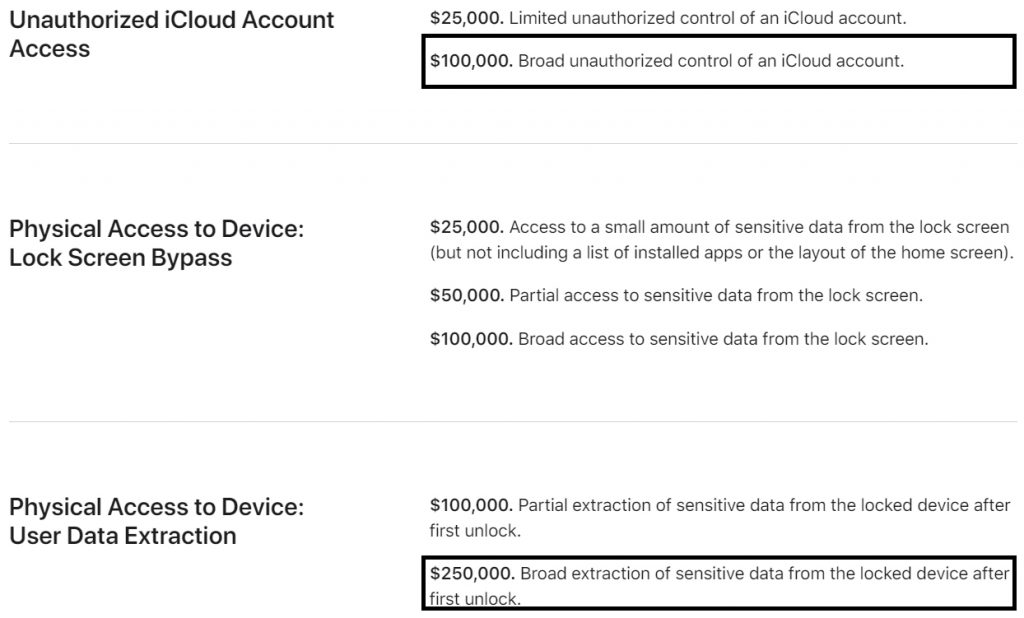
As part of the bug bounty program, the company offered the researcher a reward of $18,000, but he refused, stating that Apple had significantly downplayed the vulnerability and should have paid him $100,000 or $250,000.
The expert says that the vulnerability he found allows bypassing various security measures that Apple uses to prevent brute-forcing of passwords from accounts while using the “Forgot password” function.
So, when trying to reset the password, the user is asked to enter his phone number or email address in order to receive a one-time code of six digits. That is, an attacker who wants to hijack an account must first find out the victim’s phone number or email address, and then find out the six-digit code or go through about a million possible combinations.
To prevent possible brute-force of these codes, Apple limited the number of input attempts to five, and also limited the number of concurrent POST requests from one IP address to six. This means that an attacker would need 28,000 IP addresses to send a million requests.
The developers also blacklisted cloud services by automatically rejecting POST requests from AWS, Google Cloud, and so on.
Muthiyah found that despite these restrictions, an attacker could still send many requests if they used cloud services that were not blacklisted. As a result, the attacker will be able to pick up a six-digit code and gain access to the target iCloud account.
The researcher informed Apple about the problem back in July 2020, and it wasn’t until April 2021 that the developers prepared a patch, with the Mufti claiming that Apple did not notify him about fixing the problem.
Also, the company’s developers said that only “a very small proportion of accounts have ever been exposed to this risk, and very few users of Apple devices were vulnerable.”
Mufiya writes that the company is trying to hide the fact that the vulnerability is critical, and even made changes to the corresponding support page (after its investigation and bug report).
The researcher even discussed the problem directly with Apple engineers, who explained to him that the codes are verified on the user’s device itself and are not sent to the company’s servers, and the code verification endpoint has a limit on the number of attempts that cannot be bypassed. However, Mufiya remains convinced that the endpoint was vulnerable, and then the problem was fixed retroactively.
Let me remind you that we also talked about the fact that Apple M1 chips reveal the first bug named M1RACLES.