Malware distributors substantially increased their activity in 2019
In 2019 botnet-operators’ activity significantly grew as they launched 1,1 thousand of C&C servers a month.
These are results of quarter research of analysts from Spamhaus Malware Labs.Most often malware networks are used for sending modular spyware Trojans and remote access tools (RAT).
As say specialists, in the I quarter 2019 more than 60% of all malware activity consisted spyware Trojan Lokibot (1496 servers) and multifunctional malware AZORult (1155). Modular Trojan Pony, which closes the top three, almost 4-5 times behind the leaders.
“When we look at the number of newly detected botnet Command & Controllers (C&C), as a result of fraudulent sign-ups, it is evident that the upward trend detected in 2018 is continuing into 2019”, — noted in Spamhaus Malware Labs.
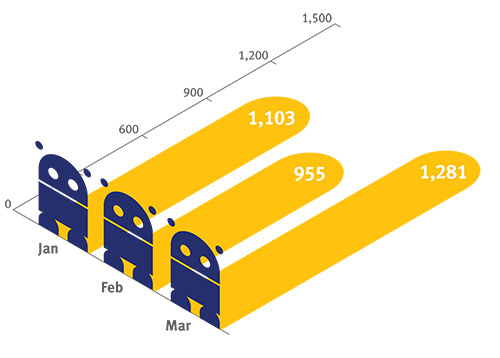
If in January 2018 experts found 276 new servers, in December their number surged to 762. Average monthly results was 530 C&C servers.
In the first quarter 2019 this figured skyrocketed more than twice and reached 1,1 thousand of C&C monthly. Only in March specialists counted about 1,3 thousands of new servers.
Their main part is traditionally located in *.com and *.uk zones. Analysts also noted growth of sites’ share under domains *.ug (Uganda) и *.ng (Nigeria).
In February every third resource in *.ug worked on intruders, while behind this activity stands only one malware service. Its operators register websites under Ugandan names and buy DNS-hosting in China.
“They register a ‘.UG’ domain name for their customer with the operator ‘i3c.co.ug’ and use a Chinese based DNS provider ‘DNSPod’ (Tencent). From a cybercriminal’s perspective, this has a big advantage: Both i3c.co.ug and DNSPod are exceptionally slow to investigate abuse reports, that’s if they are investigated at all. This makes a cybercriminal’s botnet C&C infrastructure almost 100% bulletproof to takedown requests”, — reported Spamhaus researchers.
As say Spamhaus specialists, they applied much effort and managed to decline share of unwanted web-sited under Uganda domains to 29%. Botnets most often locate on Cloudfare facilities. This hosting provider allows customers to hide location of management services and protects clients from DDoS – attacks.
Top–five also included Russian services Stajazk, Timeweb, Reg.ru and French Ovh.net.
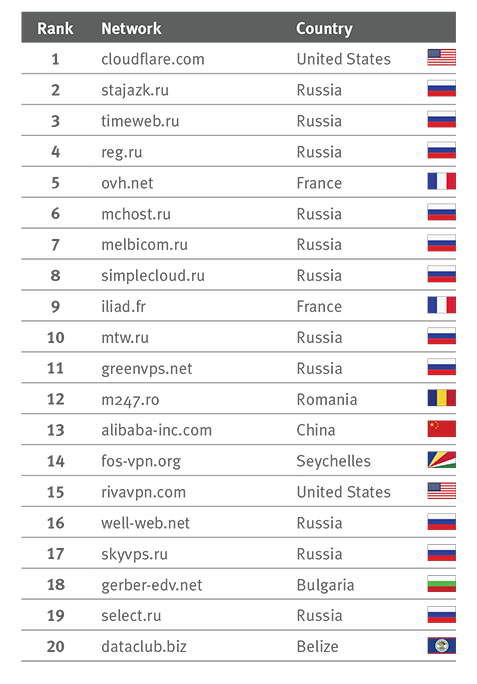
Source: https://www.spamhaus.org