Microsoft warned organizations about the dangers of the PonyFinal ransomware, which attacks have already been recorded in India, Iran and the United States.
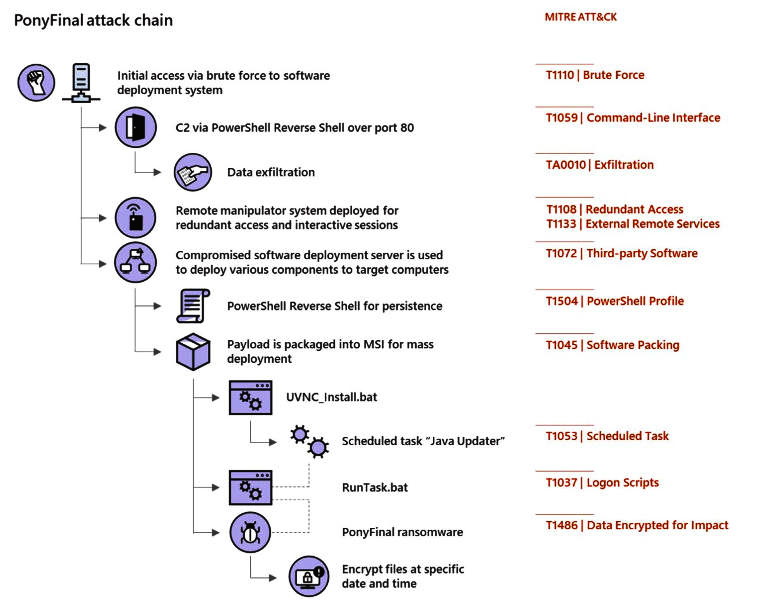
Malware is based on Java and is used for attacks that manually direct PonyFinal statements. That is, hackers break into corporate networks and manually place ransomware there, and do not distribute the encryptor automatically, through mail spam or exploit kits, as is usually the case.“Typically, the invasion point is the account on the system management server, where PonyFinal operators invade with the help of brute force attacks and the selection of weak passwords. On the server, the hackers deploy a Visual Basic script that runs the PowerShell reverse shell to collect and steal data”, — say Microsoft researchers.
Having invaded the network of the target company, the attackers spread the infection to other local systems, and then they introduce the PonyFinal ransomware itself. In most cases, hackers attack workstations on which the Java Runtime Environment (JRE) is installed, since PonyFinal is written in Java.
However, Microsoft experts note that they also recorded cases where the group independently installed JRE in the victims’ systems before launching the ransomware.
Files encrypted using PonyFinal usually have the extension .enc. The PonyFinal encryption scheme is considered reliable, as currently there are no ways and available tools to decrypt the affected data.
According to information security experts Michael Gillespie and MalwareHunterTeam, the PonyFinal ransomware appeared earlier this year, and so far few companies have suffered from its activity, which only confirms the theory that PonyFinal is used in targeted attacks on carefully selected targets.
Emsisoft specialist Michael Gillespie notes that users, which uploaded malware samples to ID-Ransomware for identification were from India, Iran, and the United States.
According to Microsoft, PonyFinal is on the short list of ransomware managed by live operators. Recently, such malware has been repeatedly used against organizations from the health sector, despite the current pandemic of the coronavirus, as was did, for example, Maze ransomware.
In addition to PonyFinal, this list includes: RobbinHood, NetWalker, Maze, REvil (Sodinokibi), Paradise, MedusaLocker and LockBit.
And live operators also rule RagnarLocker, which uses virtual machines to hide its activities.





