Researchers at IBM X-Force report that the Zeus Sphinx banker (aka Zloader and Terdot) is active again after several years of inactivity and is now exploiting the coronavirus pandemic to its advantage.
Experts recall that Zeus Sphinx was first discovered in August 2015. Then the malware went on sale in the form of a commercial modular banker, based on Zeus source code.“Then the malware focused on attacks on financial institutions in the UK, Australia, Brazil and the USA. Now Zeus Sphinx has reappeared, and it targets the same countries”, – recall IBM X-Force experts.
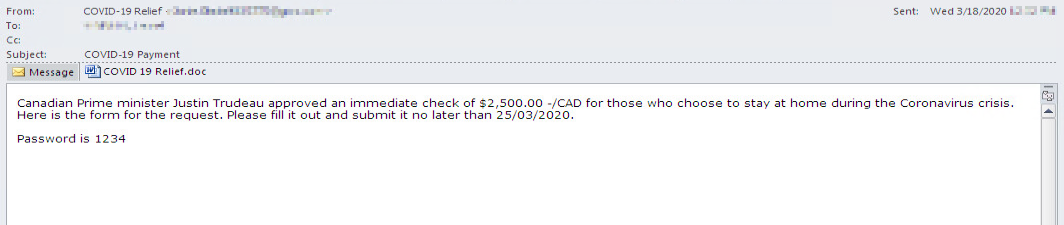
Zeus Sphinx spreads through phishing campaigns, in malicious files called “COVID 19 relief”. In their spam emails, cybercriminals claim that users are eligible for government assistance.
To receive funds, it is allegedly necessary to fill out a special form, which is attached to the message in the .DOC or .DOCX format. While downloading and opening such a document, the victim is informed about the need to enable macros, which, in turn, connect to the management server and launch the Zeus Sphinx payload.
Zeus Sphinx fixes itself in the infected system, dynamically writing itself to numerous files and folders, as well as creating registry keys. The malware also tries to avoid detection using a self-signed certificate.
Since Zeus Sphinx’s main “profile” is web injections, the malware will interfere with the work of explorer.exe and the browser, and will monitor when a user visits the landing page (for example, an online banking platform). Then the malware modifies these pages, and as a result, the user credentials are sent to the remote server that is managed by attackers.
“The infection process of the new Zeus Sphinx variant starts off with the weaponized document that creates a malicious folder under% SYSTEMDRIVE% and writes a batch file into it. After executing the batch file, it writes a VBS file to the same folder. That file is executed and uses a legitimate WScript.exe process, creates a communication channel with its C&C server and downloads a malicious executable in the form of a DLL”, – say IBM X-Force experts.
I must say that the activity of Zeus Sphinx operators is only one of many cases when cybercriminals exploit the COVID-19 theme. For example, Maze operators attacked medical company, which is testing vaccine for COVID-19. Cybercriminals also spread malware through Zoom Fake Domains. The time of real and virtual viruses requires increased attention to personal security and the storage of personal data.





