Ransomware Victims Are Less Likely to Pay Hackers
According to statistics from Coveware, victims have become less likely to pay hackers: ransom paid to ransomware operators has been declining since the last quarter of 2021.
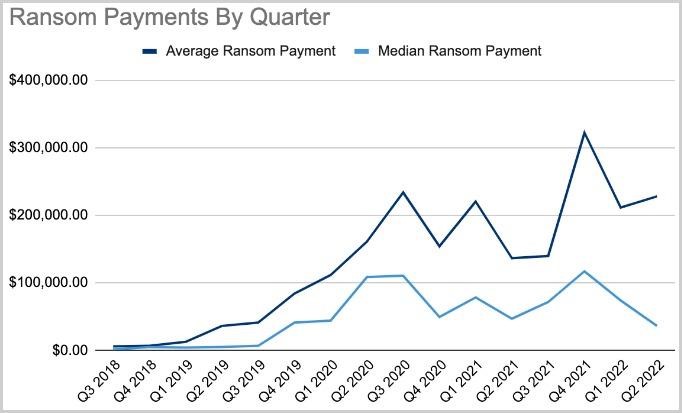
Thus, in the second quarter of 2022, the average ransom amount was $228,125 (8% more than in the first quarter of 2022). However, the median ransom was only $36,360, down 51% from the previous quarter.Let me remind you that we also wrote that North Korean Ransomware Maui Attacks Healthcare Companies.
According to Coveware analysts, the downward trend began at the end of last year, when there was a peak in payments to ransomware operators on both the average ($332,168) and median ($117,116) values.
Payment amounts
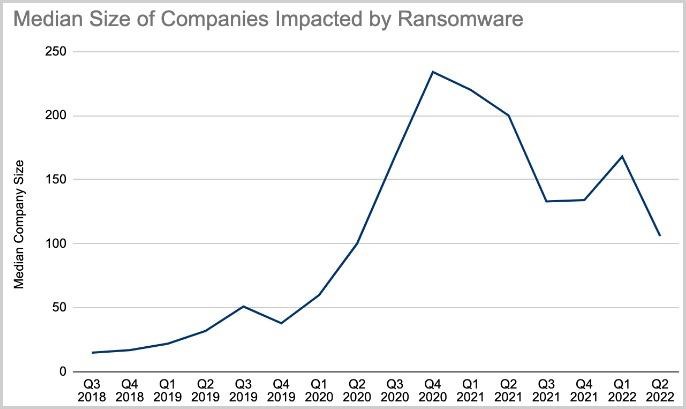
The researchers explain that RaaS operators and developers are attacking medium-sized companies and organizations, as this is associated with fewer risks. In addition, experts speak of an “encouraging trend” when large companies simply refuse to negotiate with attackers if they demand incredibly large ransoms.
This quarter, the average size of a victim company dropped even further this quarter, Coveware said, as hackers are now looking for smaller but financially healthy organizations to run their operations.
Victim company sizes
Analysts emphasize that in many cases, attackers still continue to extort or publish files stolen from the company even after receiving a ransom. In many cases, data theft was the main method of extortion at all, that is, many incidents were not related to file encryption. This resulted in the average downtime due to ransomware attacks being reduced to 24 days, down 8% from Q1 2022.
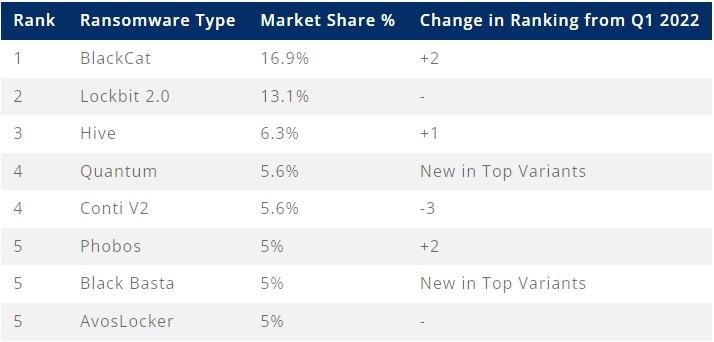
The list of the most active ransomware groups in Q2 was led by BlackCat (aka ALPHV), which accounted for 16.9% of all known attacks, followed by LockBit, which accounted for 13.1% of incidents.