TP-Link router botnet was sending weird SMS since 2016
At the Virus Bulletin 2021 conference, Acronis and Search-Lab experts spoke about a botnet consisting of TP-Link routers. Since 2016, he has abused the device’s built-in text messaging function, and its operators have offered SMS messaging services.
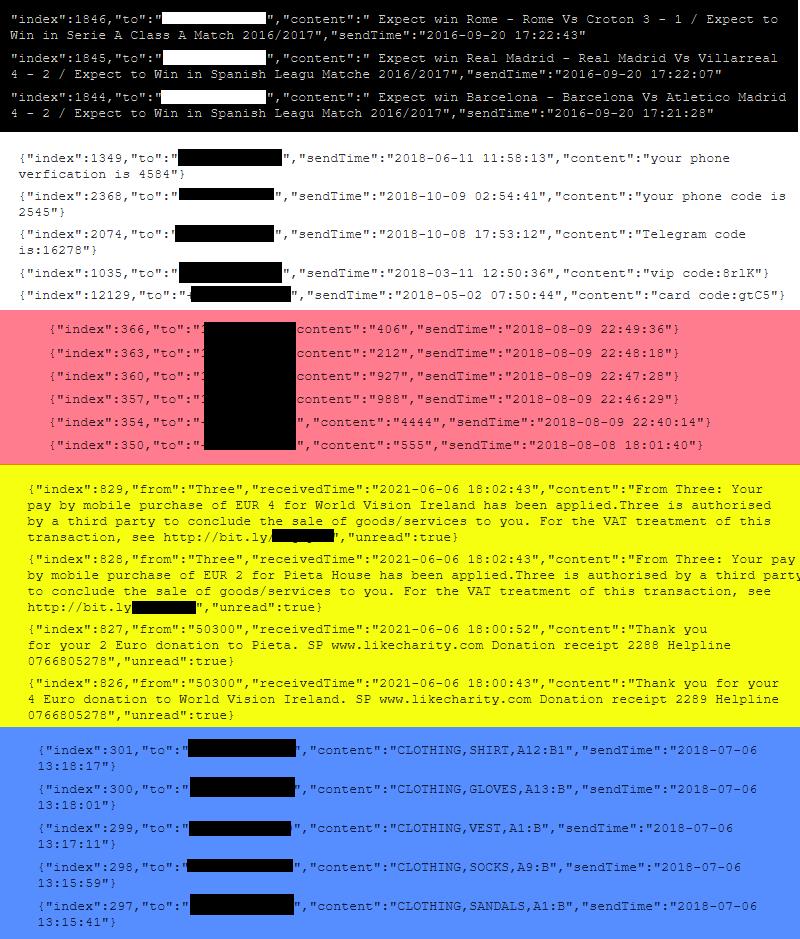
Over the years, infected routers have been used to send out betting tips, verification codes, confirm online payments and donations, and send cryptic messages that researchers haven’t figured out yet.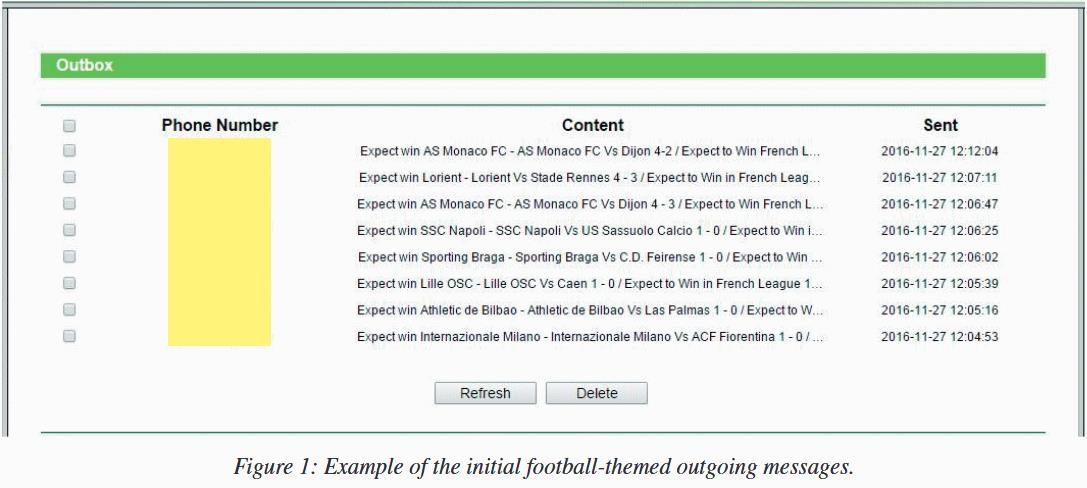
One of the report’s authors, Robert Neumann, told The Record that he became aware of the botnet back in May 2018, when he was asked to investigate a compromised 4G router. The device generated a huge amount of outgoing SMS, which were sent from the built-in SIM-card, and its owner received impressive communication bills.
As a result, this investigation became one of the most complex and confusing in Neumann’s career, it lasted three years and included the collection of evidence and logs of several victims, as the researcher decided to build a big picture and trace the attacks and operations of the botnet.
To begin with, the expert figured out how the hackers infiltrated the devices. It turned out that the attackers exploited a vulnerability discovered back in 2015. It could be used to access files on TP-Link routers without prior authentication. Although this bug was fixed in later versions of the firmware, Neumann says there were still thousands of devices available on the network, many of which are still vulnerable to this day.
As a result, the expert was able to reproduce the exploit for the 2015 vulnerability and gained access to one of the router’s functions, which was responsible for “sending SMS messages, reading incoming and outgoing SMS messages, collecting information about SIM-lock, and changing LAN and time settings.” This interface has only been found in TP-Link MR6400 devices, 4G routers that were usually installed in places where wires could not be used.
As a result, the attacker who hijacked the routers built an easy-to-manage botnet on their basis, and then began offering services to send cheap text messages to other people. Although the researchers were unable to locate advertisements for this service, the sheer variety of SMS campaigns suggests that the botnet operator has a wide customer base.
Who built this botnet is still a mystery, since the network of hacked routers provided complete anonymity to its creators, which could only monetize the botnet by charging a small fee from their customers.
Let me remind you that we talked about the fact that Operator of the proxy botnet Russian2015 pleaded guilty, as well as that Emotet botnet self-destructed on all infected machines.





