Hackers Attacked the British Company South Staffordshire Water, but Mistakenly Demanded Money from Another One
The British company South Staffordshire Water, which supplies 330 million liters of drinking water daily to approximately 1.6 million consumers, reported that its IT systems were disrupted as a result of a hacker attack. At the same time, Clop ransomware operators said they attacked Thames Water, the country’s largest provider of water and wastewater treatment services. Apparently, the hackers confused the two companies.
Let me remind you that we also reported that the US authorities were talking about three ransomware attacks on water treatment plants.Bleeping Computer reports that an official statement has appeared on the South Staffordshire Water website confirming the hacker attack. The water company explains that its water security and distribution systems are operating as normal, so the outage will not affect the water supply of its customers and subsidiaries, including Cambridge Water and South Staffs Water.
South Staffordshire Water also assured that all service crews are working as usual, and there is no risk of long-term water outages due to a cyber attack.
At the same time, a message appeared on the site of the extortionist group Clop on the dark web about the hacking of Thames Water. Allegedly, hackers gained access to its SCADA systems, which they could manipulate to harm 15 million customers.
As mentioned above, Thames Water is the UK’s largest provider of water and wastewater services, serving Greater London and the areas around the Thames.
In their statement, the hackers emphasize that they notified Thames Water about security problems and acted responsibly, that is, they did not encrypt data, but “only” stole about 5 TB of information from compromised systems.
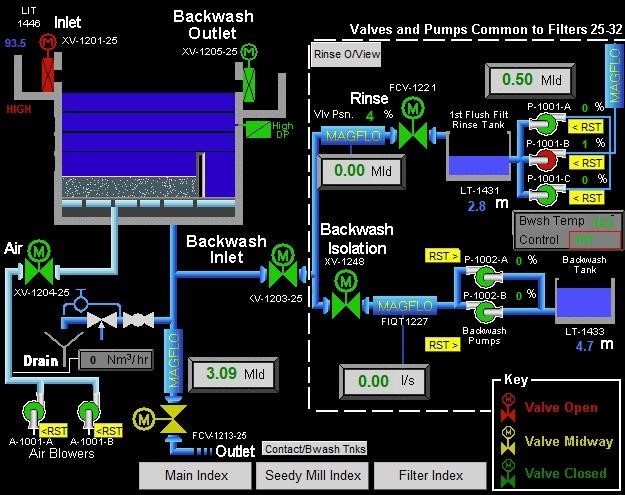
The group claims that negotiations with the company to pay the ransom were unsuccessful, and therefore the first sample of stolen data was published on the group’s website, which included passports, driver’s licenses, screenshots of water treatment SCADA systems and much more. At the same time, experts confirm that the screenshots are taken from a real system that is used to control chemicals in the water treatment process.
However, representatives of Thames Water issued an official statement in which they called the words of the hackers a lie, assuring that this was a “cyber hoax” and that all the company’s systems were operating at full capacity.
Bleeping Computer journalists say that, apparently, the hackers simply made a mistake and extorted money from another company. The fact is that even in the dump published by Clop, you can find documents and a spreadsheet with usernames and passwords, in which the email addresses of South Staff Water and South Staffordshire PLC appear, and not Thames Water at all.
After the media spotted the ransomware bug, the hackers rushed to fix it, and the Clop site now lists South Staffordshire Water as a victim. At the same time, it is not clear whether the group really tried to extort money from another, larger company, or whether the case was limited to an error when publishing the dump.