Children’s smart watch SMA-WATCH-M2 discloses personal data and location information
For several years, AV-TEST researchers have been studying the safety of smart watches for children. This time, experts checked the budget gadget SMA-WATCH-M2, created by the Chinese company SMA and concluded that the watch discloses personal data, and indeed its protection should be reinforced.
A $ 35 watch reveals personal information about more than 5,000 children and their parents.Researchers say that SMA-WATCH-M2 are designed to work in tandem with the corresponding application. So, parents register an account, connect the child’s smart watch to their phone and use the application to track their location, make voice calls or receive notifications when the child leaves a certain area.
Read also: A previously unknown GPS attack creates “ghost ships”
There are many similar gadgets on the market, cost of which varies from $ 30 to $ 300, but experts write that the SMA has created one of the most unsafe products in this area.
“Anyone can request a smartwatch backend through a public API. This is the same backend to which the mobile application connects to extract the data that is displayed on the parents’ phones. Although it would seem that for these operations there is an authentication token that supposedly should prevent unauthorized access, in fact, attackers can provide any token, since the server simply does not verify its validity”, – found researchers from AV-TEST.
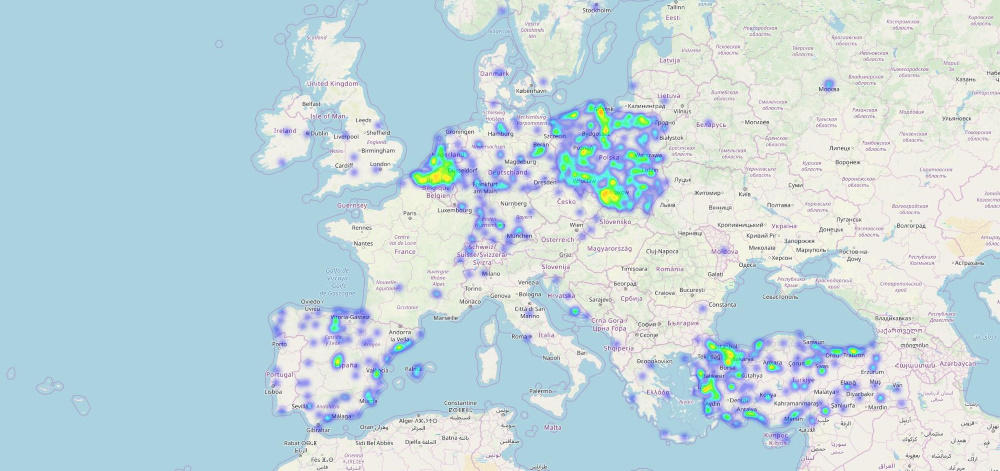
As a result, an attacker can connect to the API, examine user identifiers and collect data about children and their parents. Therefore, he can find out the child’s current geographic location, device type, and IMEI SIM card. In this way, AV-TEST analysts were able to identify more than 5,000 owners of smart watches and more than 10,000 parental accounts. Majority of the children were identified in Europe, in countries such as the Netherlands, Poland, Turkey, Germany, Spain and Belgium, but also active smart watches were found in China, Hong Kong and Mexico.
The mobile application installed on the parents’ phones was also extremely insecure. The fact is that the attacker can install the application on his own device, change the user ID in the configuration file and associate his smartphone with the smartwatch of someone else’s child, without even entering an email address or password from the parental account. Next, the application functions could be used to track a child using a card, make calls and start voice chats with children.
“Worse, an attacker can change the password for an account and block the application of real parents while he communicates with the child”, – report experts from AV-TEST.