Researchers present tools for scanning computers for BlueKeep vulnerability
Last month Microsoft announced that it had discovered a vulnerability in remote desktop services that could allow malicious malware to spread easily through vulnerable systems.
This vulnerability, now known as BlueKeep, was given a unique identifier, CVE-2019-0708, and affects Windows 7, Windows 2008 R2, Windows Server 2008, Windows XP and Windows Server 2003.Considering severity severity of the problem, Microsoft released patches for all supported versions of Windows, and even for those that the company no longer supports as Windows XP and Windows Server 2003.
Since that time, many security researchers rushed to create experimental exploits that can be used by BlueKeep. Of course, there is confidence that the attackers do not sit quietly.
Read also: BlueKeep still can attack about one million of computers
Knowing that exploit of cybercriminals inevitably would be created, Microsoft issued a second warning, and the National Security Agency (NSA) issued its own council, urging Windows users to patch the system immediately.
Bleepingcomputer journalists offer two tools with which you can check if your Windows machine is vulnerable to BlueKeep.
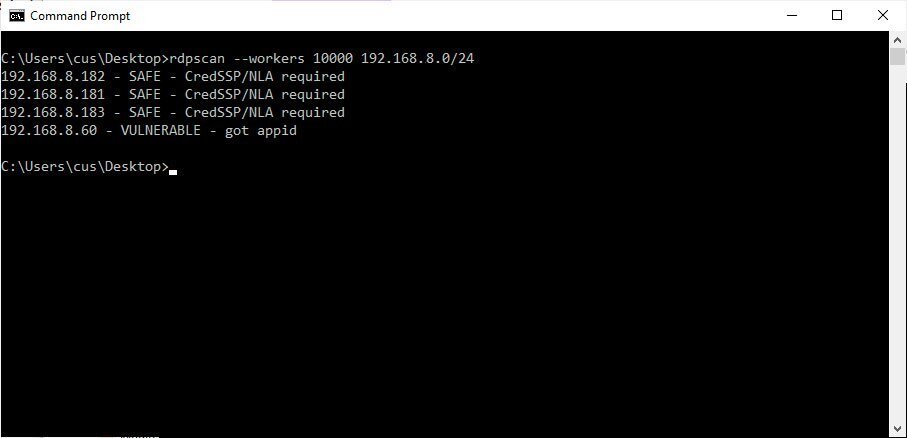
Security researcher Rob Graham created a program called RDPScan for Windows and macOS based on the Zdesos0x0 rdesktop patch.
To use RDPScan, simply download the latest version from the project’s release section. After downloading, you can start the program from the command line using the following commands:
rdpscan [ip_address] rdpscan 192.168.1.29
Scan a range of IP addresses:
rdpscan [start_ip_address]-[end_ip_address]
rdpscan 192.168.1.29-192.168.1.100
Scan a network with CIDR notation:
rdpscan [network]/[cidr_notation]
rdpscan 192.168.1.0/24
RDPScan will check each of the IP addresses to determine if port 3389 is open, and then determine if the computer is vulnerable. To change the port that is scanned, can be used -p argument. You can also use the –workers argument to increase the scanning speed.
For a complete list of arguments, use rdpscan -h.
While scanning for vulnerabilities, list of hosts will indicate “Safe”, “Vulnerable” or “Unknown”. Appropriate security updates must be installed on all hosts marked as vulnerable.
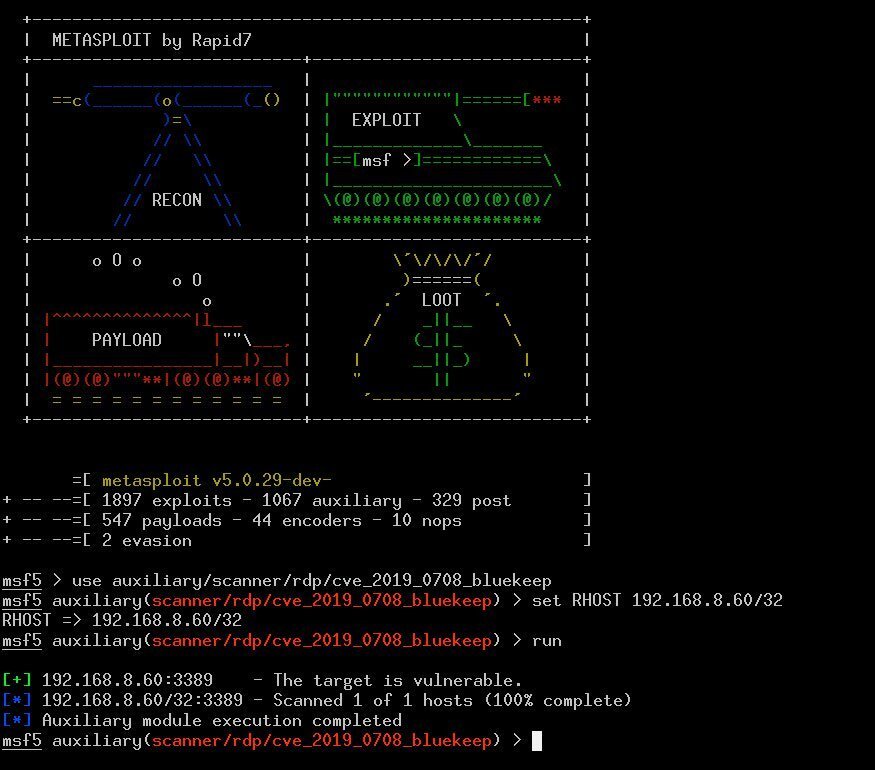
For users of the penetration testing infrastructure from Metasploit, security researchers Zerosum0x0 and JaGoTu have also created a module that can be used to scan for the BlueKeep vulnerability.
If Metasploit installed, you can load the module with the following command:
After the module is loaded, you can scan individual systems and networks.
Source: https://www.bleepingcomputer.com





