Compromised npm Packages Use Cryptocurrency Exchanges
Unknown attackers compromised the account of one of the developers of the dYdX cryptocurrency exchange and injected malicious code into several npm packages that, in addition to dYdX itself, use at least 44 cryptocurrency exchanges.
The creator of Diffend.io Maciej Mensfeld from Mend noticed the problem. He said that he found several compromised npm packages that secretly installed infostealers on victims’ machines.Apparently, the malicious packages were published under the account of a dYdX employee who was compromised by hackers, although the exact reason for the appearance of the malicious code is still unclear. The malware was seen in @dydxprotocol/solo (versions 0.41.1, 0.41.2) and @dydxprotocol/perpetual (versions 1.2.2, 1.2.3) packages. It was also reported that the @dydxprotocol/node-service-base-dev package was also affected by the attack, but it has since been withdrawn.
The main problem is that these packages are used not only by dYdX itself, but also by 44 other cryptocurrency projects.
Let me remind you that we also wrote that The Developers of the Nomad Cryptocurrency Bridge Ask the Hackers to Return the Money and… They Return.
Mensfeld and Bleeping Computer showed a piece of problematic code embedded in the manifest file of the solo package. Once the package is installed, a script will run that will download and run the contents of the ci.js JavaScript file hosted on api.circle-cdn.com, which in turn will download another Python script (setup.py). The researcher warns that this script contains code that steals credentials and other secrets, including GitHub tokens, SSH keys, environment variables, and also learns the victim’s external IP address.
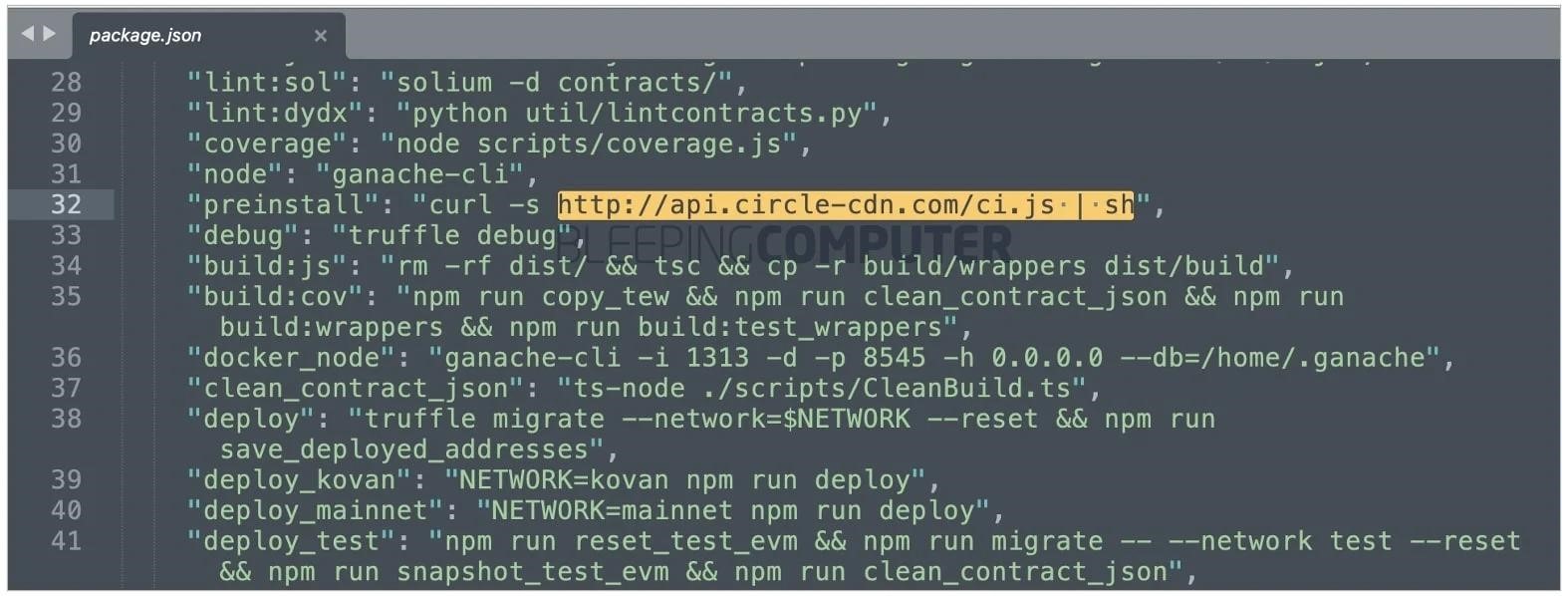
It is noted that the circle-cdn.com domain was registered quite recently – on September 14 of this year. It is assumed that using such a domain name and a file called ci.js, hackers are trying to imitate CircleCI.
dYdX Chief Architect Brendan Chou has already thanked the expert for his vigilance and confirmed that “all compromised package versions have already been removed.” Only [email protected] remained unremoved, but Chow writes that this is a “temporary oversight” on npm’s part.





