CyberArk specialists discovered a vulnerability, with the help of which could be compromised account of the Microsoft Teams platform, designed for communication and collaboration. For this, the attackers needed to send a link or a gif to an employee of the target organization.
Although it was not difficult to send a malicious link or GIF, the preparatory stages of this attack included several steps that would not be possible to carry out for inexperienced hackers.“In connection with COVID-19, cybercriminals became more active, as the pandemic forced many companies to switch to remote work, which also led to a significant increase in the number of users of Microsoft Teams or other similar platforms. Even if the attacker doesn’t get a lot of information from the Microsoft Teams account, he will be able to use this account to move in the organization’s network”, – say the experts.
The discovered vulnerability was related to the way the desktop and browser versions of Microsoft Teams work with authentication tokens and image resources. In fact, the attacker could create a link or GIF file, which, when processed by Microsoft Teams, transferred the user’s token to the server controlled by the attacker.
And if, when using the link, the victim had to click on it, then in the case of the GIF file, the victim was just to see the gif in Microsoft Teams chat, after which the token was sent to the hacker. That is, the attack did not require interaction with the user.
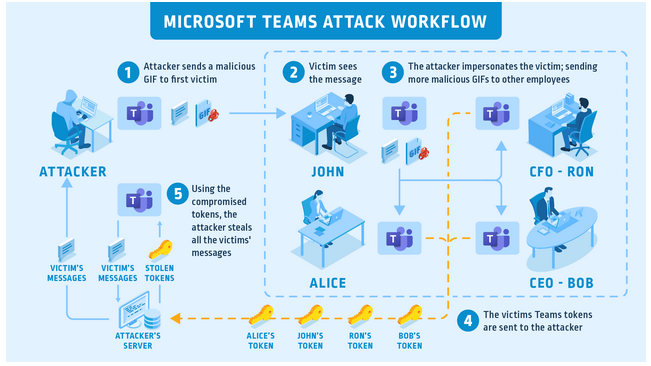
Having seized the authentication token, the attacker was able to use it to steal the victim’s account using the APIs.
This method was suitable for reading user messages in Microsoft Teams, sending messages on behalf of the victim, creating groups, adding or removing users from groups, and changing group permissions.
Worse, the attack could be fully automated, which could cause spreading of the problem throughout the organization like a worm, using compromised accounts to send malicious GIFs to other Microsoft Teams users. In this way, an attacker could gain potentially sensitive information, including passwords, meeting and calendar data, and business plans.
“What is even more alarming, this vulnerability could also be used to send false information to employees (posing as one of the company’s leaders), which could entail financial damage, confusion, direct data leaks, and so on”, — write CyberArk researchers.
So, the researchers describe simple examples of the vulnerability: an attacker uses a hacked account to request a password reset from the organization’s IT department. An attacker also contacts the CEO using a hacked account from another manager and asks for confidential financial information. In the same way, an attacker can try to convince the CEO, for example, to install a malware on his cars.
Speaking about mentioned above limitations mentioned, it must be said that when a victim sees a malicious GIF file, its access token can only be sent to the teams.microsoft.com subdomain, which means that the attacker needs somehow compromise such a subdomain.
Let me remind you that recent warnings of information security experts said that hundreds of legitimate Microsoft subdomains could be hijacked and used for phishing, delivering malware and all kinds of fraud. However, in case of an attack on Microsoft Teams, the attacker will need to find the teams.microsoft.com subdomains.
CyberArk researchers acknowledge that this is not an easy task, but they believe that attackers, which are possessing necessary resources and methods, can do it. The experts themselves found two subdomains that could be used for attacks: aadsync-test.teams.microsoft.com and data-dev.teams.microsoft.com.
Returning to the restrictions, it is necessary to mention that in order to start the attack, the attacker needs to gain access to the Microsoft Teams account, from which he can start sending malicious links or GIF files. That is, you will need to pre-compromise one of the company’s employees in a different way.
However, the researchers are confident that the attack can still be launched from outside the target organization. For example, an attacker could convince a victim to invite him to Microsoft Teams for an interview.
Recall that Researchers found that employees ’errors are the main cause of cybersecurity incidents and problems.
Microsoft reports that discovered by specialists vulnerability has already been eliminated, and discovered by CyberArk subdomains can no longer be used by attackers. The company also said that they did not find any signs of exploitation of this error by real hackers.





