Maze ransomware operators leaked data on Costa Rica bank customers
Bleeping Computer reports that the hacker group behind the operations of the Maze ransomware published in public domain on its website credit card information, stolen from Banco de Costa Rica.
Since the bank’s management denies compromising, hackers are threatening to continue to publish such dumps every week until they are paid a ransom. In an interview with reporters, Maze operators noticed that they demanded a ransom from the bank several times, and, in theory, they could sell information about cards on the darknet.“We have at our disposal the data of 11 million cards issued by Banco de Costa Rica, approximately 4,000,000 of which are unique, and about 140,000 belong to US citizens”, — said Maze operators on April 30, 2020.
Hackers claim that they first got access to the bank’s network back in August 2019, and then again, in February 2020, to “check if security has improved”. At the same time, the attackers did not encrypt the files of the financial institution, as they considered that doing such during a pandemic was wrong and “the possible damage would be too great.”
Maze operators promised not to attack medical facilities during the pandemic, but soon the promise was broken and hacked the medical center, which is testing the vaccine against COVID-19.
However, the group was not left empty-handed after attacking bank network, having stolen the card data.
The now published 2GB dump that contains Banco de Costa Rica payment card numbers. Hackers write that publishing this data in the public domain, they are not trying to earn on this, but they want to draw attention to the bank’s security problems.
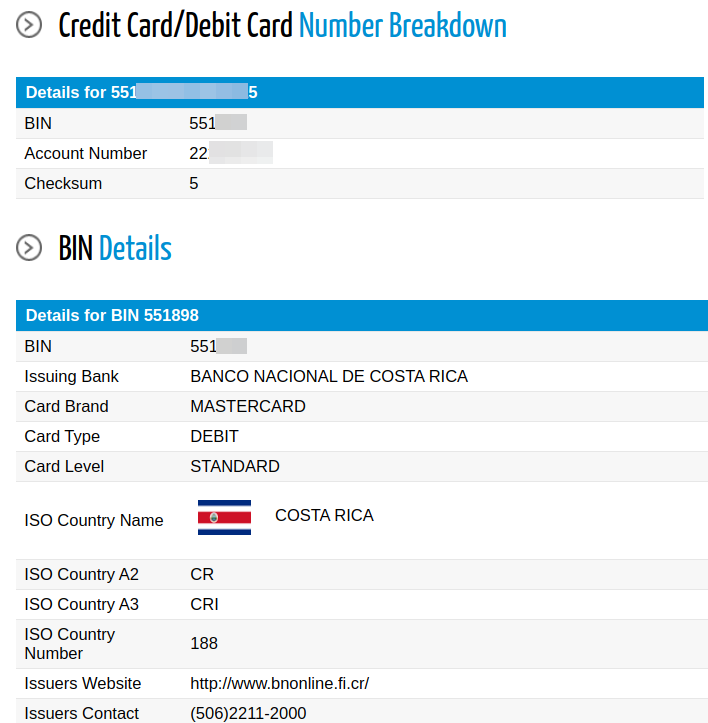
Screenshots of the contents of the database, showing unencrypted bankcard numbers, were attached to the hackers’ message.
“In total, images contain data of at least 50 cards (some are listed several times). It’s also worth noting that earlier Maze operators published more than 100 partial card numbers (the last four digits are deleted) with the expiration date and CVV codes”, – writes Bleeping Computer magazine.
Bleeping Computer researchers tested several cards through special online services, and majority passed the test. The bank identification number (BIN) showed that these are Visa and MasterCard debit cards, actually issued by Banco de Costa Rica.
Interestingly, representatives of Banco de Costa Rica still deny the fact of compromise. So, back in early May, the bank issued an official statement, according to which, after a full audit, representatives of Banco de Costa Rica were able to confirm that “the institution’s systems were not compromised.”
At the end of last week, the bank made another statement, again informing that numerous checks, conducted by both the organization’s own specialists and invited experts showed that no one had access to the bank’s systems without authorization and “customer transactions were not affected.”
Recall that Doppel Paymer operators, Maze colleagues in crimes, published in the public domain Boeing, Lockheed Martin, SpaceX and Tesla documents.