Famous cybersecurity expert and founder of Sanguine Security (SanSec) Willem de Groot warned about the largest attack in the company’s history aimed at compromising online stores based on the e-commerce platform Magento. According to the specialist, stores based on Magento have suffered the largest attack since 2015.
All of these attacks were typical of MageCart hackers: attackers hacked websites and injected malicious scripts into their code, recording and stealing bankcard data of users, which they entered during ordering.“Last Friday, 10 stores were infected, followed by 1058 on Saturday, 603 on Sunday, and 233 more today. This automated campaign is the largest ever detected by Sansec since the start of observations in 2015. The previous record was 962 hacked stores in one day in July last year”, — de Groot wrote on Monday, September 14, 2020.
Let me remind you that initially the name MageCart was assigned to one hack group, which was the first to introduce web skimmers (malicious code) on the pages of online stores to steal card data. However, this approach was so successful that the group soon had numerous imitators, and the name MageCart became a common name, and now denoting a whole class of such attacks.
SanSec experts write that most of the hacked sites used the outdated version of Magento 1.x, whose support was finally discontinued on June 30, 2020. Interestingly, even last year, cybersecurity experts predicted an increase in attacks on Magento 1.x, expecting the rise to from 200,000 to 240,000 of vulnerable resources. Fortunately, the number of vulnerable sites has decreased since then, and currently it is about 95,000.
ZDNet also recalls that this summer, some information security specialists expressed concern that new vulnerabilities in Magento 1.x had not been discovered for a long time. The fact is that it is untypical picture, since the 1.x branch has long been considered old and full of bugs.
“The hackers deliberately kept their Magento 1.x exploits on hold and waited until the end of the support period to make sure that the Adobe developers did not fix the vulnerabilities”, — feared the experts.
It looks like these experts were right.
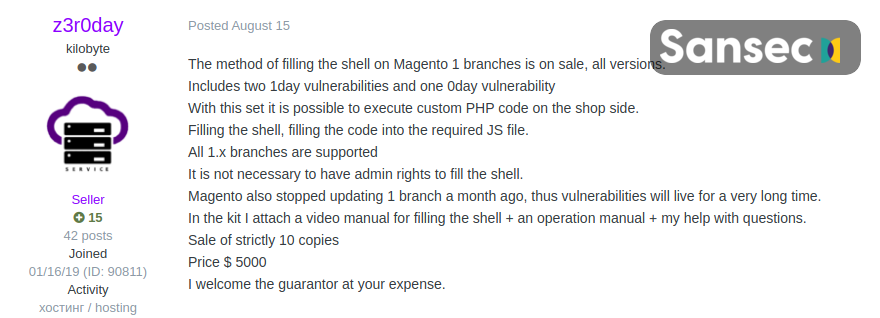
While SanSec analysts have yet to establish exactly how the hackers entered the affected sites, Willem de Groot writes that an advertisement for a zero-day vulnerability in Magento 1.x appeared on hacker forums last month, also confirming that the hackers were biding their time. In the ad, someone named z3r0day offered an RCE exploit for $5,000.
Let me remind you that IS experts discovered the link between North Korean hackers and MageCart attacks.





