IIS Extensions Are Increasingly Being Used as Exchange Backdoors
Microsoft says attackers are increasingly using malicious Internet Information Services (IIS) web server extensions as backdoors to bypass unpatched Exchange servers because they are harder to detect than web shells.
Malicious extensions are hidden deep inside compromised servers and are very difficult to detect. When installed in the right place and using the same structure as legitimate modules, extensions provide a perfect and reliable persistence mechanism for a cybercriminal.Let me remind you that we also wrote that Information security experts have accused Chinese hackers of massive indiscriminate and automated cyberattacks on Microsoft Exchange servers around the world.
Typically, malicious extensions are launched after the web shell is deployed as the first payload in an attack. The IIS module is deployed later to provide silent and update-tolerant access to the compromised server. Once deployed, malicious IIS modules allow an attacker to extract credentials from system memory, gather information from the victim’s network, and deliver additional payloads.
Between January and May 2022, in an attack on Microsoft Exchange servers, attackers deployed malicious IIS extensions to gain access to victims’ email inboxes, remotely execute commands, and steal sensitive data.
According to a Microsoft report, after reconnaissance, resetting credentials, and establishing a remote access method, the cybercriminals used a special IIS backdoor “FinanceSvcModel.dll” that could perform Exchange management operations such as listing established mailbox accounts and exporting mailboxes for exfiltration.
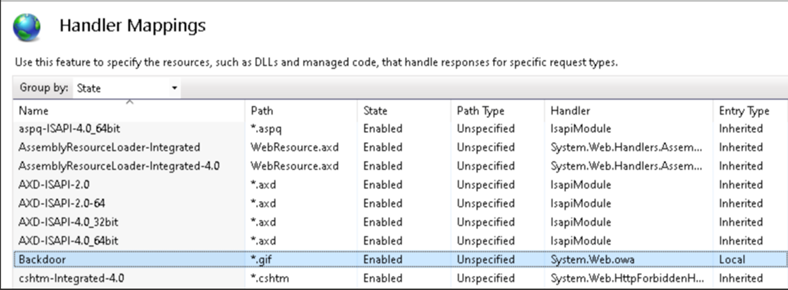
According to Microsoft, IIS modules are not a common format for backdoors, especially when compared to typical web application threats such as web shells, and are therefore easy to miss with standard file monitoring.
To protect computers against attacks using malicious IIS modules, Microsoft recommends that customers take the following steps:
- keep your Exchange servers up to date;
- keep anti-virus programs enabled;
- check confidential roles and groups;
- restrict access to IIS virtual directories;
- set the priority of warnings;
- check configuration files and bin folders.
Let me also remind you that WSJ Says Microsoft Partners May Be Involved in Cyberattack on Exchange Servers.





