Hackers attacked airline via Slack API
IBM Security X-Force experts believe Iranian “government” hackers are deploying the recently discovered Aclip backdoor to victims’ networks, which attacks through the Slack API to covertly communicate with criminals.
According to the report, the attackers are the ITG17 hacker group, also known as MuddyWater, attacking organizations and companies around the world. The cybercriminals discovered by IBM Security X-Force began operating in 2019, when they targeted an unnamed Asian airline to steal flight booking data.By the way, we also reported that Hackers used Slack to hack Electronic Arts computer systems.
According to experts, Slack is almost an ideal platform for hiding malicious communications, since data is mixed with normal business traffic, and Slack is widely used in a variety of fields. In this case, the Slack API was used by the Aclip backdoor to transfer system information, files and screenshots to attackers, receiving commands from their operators in response.
IBM researchers noticed attackers abusing this communication channel in March 2021 and reported this to the Slack developers. Those, in turn, quickly reacted to the report of the researchers and assured:
The detected Aclip backdoor is executed using the aclip.bat file, and this is where its name comes from. The backdoor provides cybercriminals with a constant presence on the infected device, as it is added to the registry and launched automatically at every system startup.”
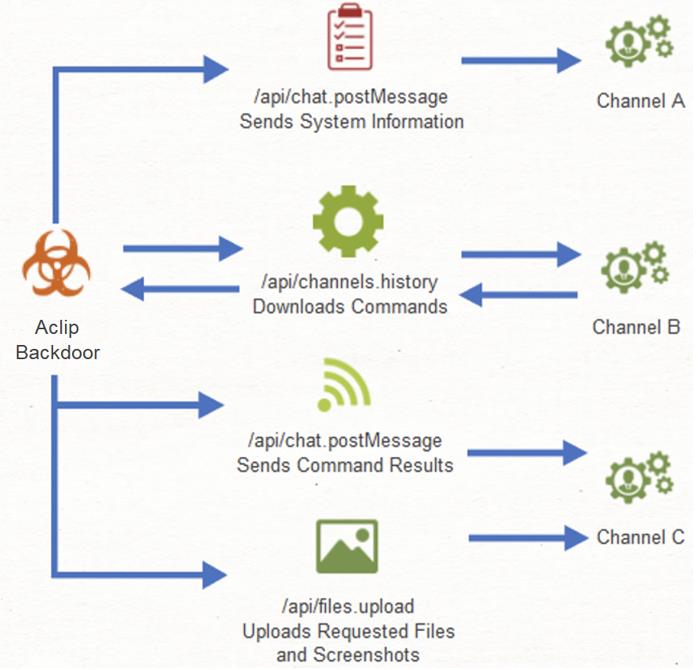
Aclip receives PowerShell commands from the C&C server via the Slack API and can be used to execute further commands, send screenshots of the active Windows desktop, and steal files.
We also wrote that Iranian hackers disguised themselves as an aerobics instructor.





