In the spring this year, Google Project Zero experts found 14 vulnerabilities in iOS, which were grouped into five exploit chains and have been used against users since 2016.
Although vulnerabilities in iOS are usually used in a targeted manner to crack specific targets, in this case, malicious sites remotely attacked all users who visited resources using the iPhone, without any interaction with their victims.“There was no discrimination: just visiting the hacked site was enough for the exploit server to attack your device and, if the attack succeeded, install an implant for monitoring”, — says Ian Beer, experts at the Google Project Zero team.
According to Google, the first site that hosted the exploits was put into operation on September 13, 2016. It seems that all malicious sites were simply hacked by attackers, and exploits on them were posted by attackers, rather than by the owners of the resources themselves. According to researchers, malicious sites totaled thousands of visitors per week. Researchers do not disclose addresses and names of resources.
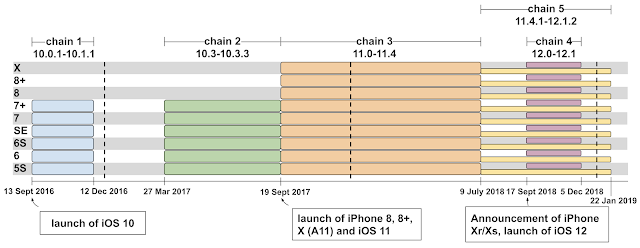
Google experts warned of problems that found Apple engineers and which led to the release of iOS 12.1.4 in February 2019, when the vulnerabilities were fixed. The researchers report that seven of the problems they discovered affected the iPhone browser, five on the core, and two more allowed escaping from the sandbox. The exploits were intended for iOS versions 10.x, 11.x and 12.x.
Beer and his colleagues at Google Project Zero have already published a detailed analysis of all five exploit chains (1, 2, 3, 4, 5), and also spoke in detail about the JSC exploit, with which hackers carried out an initial attack on the browsers of the victims. Was also published an analysis of the implant (malware), which as a result of attacks infected victims’ iOS devices. This implant could steal the victim’s personal data, including iMessages, contacts, photos and device location information in real time.
Read also: iOS URL schemes allow conducting App-in-the-Middle attack
Fortunately, the malware could not maintain a constant presence on the device, and simply restarting the iPhone eliminated the infection (until the user again visited one of the hacked sites).
While most exploits targeted old vulnerabilities that Apple had already fixed earlier, at least one of the exploit chains used 0-day. This concerned CVE-2019-7287 and CVE-2019-7286, fixed as part of iOS 12.1.4 in February 2019.
“I will not discuss whether these exploits are worth a million dollars, two million or twenty. Instead, I notice that all of these amounts seem low for the possibility of real-time targeted attacks and monitoring the personal activity of the entire population”, — Bir summarizes.
Experts believe that other similar malicious campaigns and exploits may exist, and discovered sites on Google are called an accidental failure for attackers.






One Comment