Miners Massively Use Free GitHub, Heroku and Buddy Accounts in Their Campaigns
Sysdig specialists have discovered the Purpleurchin campaign, whose operators were abusing free accounts in GitHub, Heroku and Buddy services to mine cryptocurrency at their expense.
Let me remind you that we also wrote that Cryptocurrency scammers force victims to record videos to attract new victims.Attackers use free cloud accounts to make tiny profits, but many of these accounts combined can generate significant income for fraudsters.
The researchers said that the Purpleurchin campaign makes over a million function calls daily using GitHub (300 accounts), Heroku (2000 accounts), and Buddy.works (900 accounts).
These accounts are interleaved and routed through 130 Docker Hub images with mining containers, and heavy obfuscation at all levels has long kept the scammers undetected.
According to Sysdig, the core of this operation will be the linuxapp container (linuxapp84744474447444744474), which acts as a control server and a Stratum server, coordinating all active mining agents and directing them to a pool of attackers.
The userlinux8888 shell script is used to automate the creation of GitHub accounts, the creation of repositories, and workflow replication using GitHub Actions. At the same time, all GitHub Actions are obfuscated using random strings for names.
In addition, Purpleurchin operators use OpenVPN and Namecheap VPN to register accounts under different IP addresses to avoid detection of their activity.
More than 30 instances of Docker images are launched using GitHub Actions, predefined arguments are used to run the script, the IP address and port of the proxy server to connect to, the name of the Stratum ID, and the maximum amount of memory and CPU to use.
Finally, another script (linuxwebapp88) checks the configuration on the Stratum server, gets the Docker command contained in the GitHub repository, and starts the mining container.
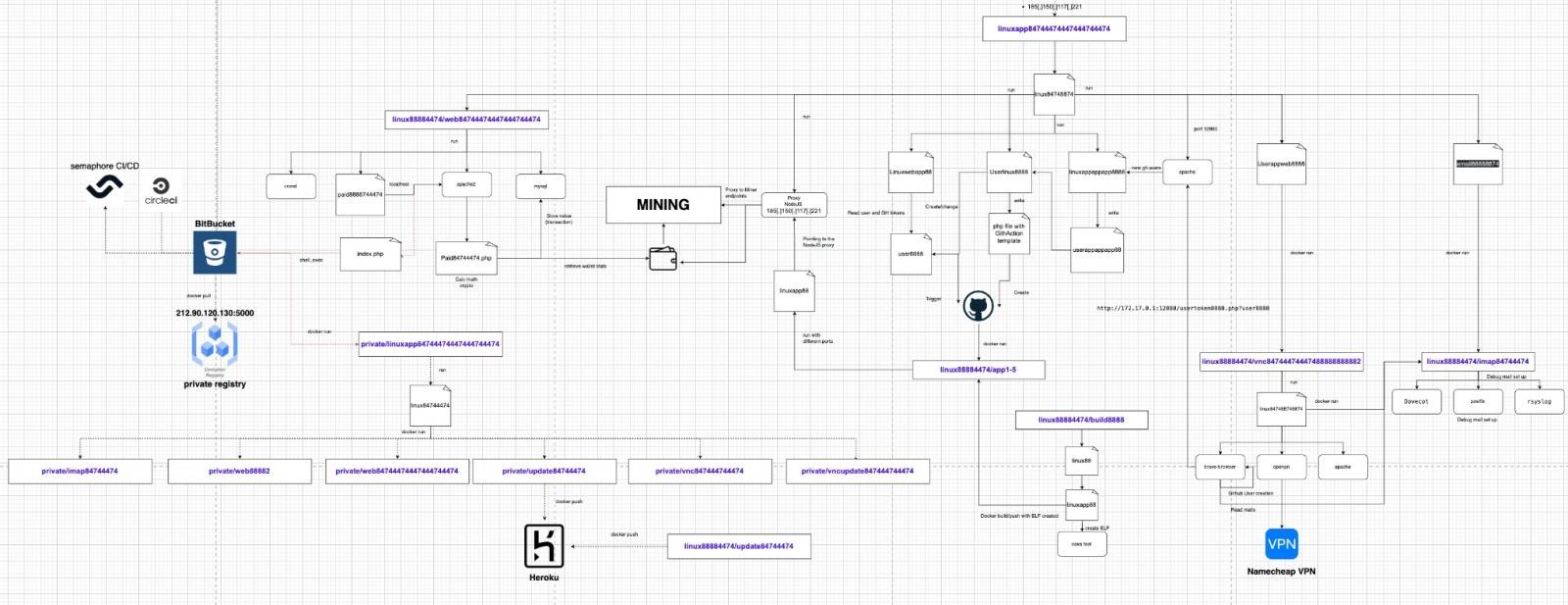
General scheme Purpleurchin
The rogue miner uses a small portion of the server’s CPU power to stealthily mine various cryptocurrencies, including Tidecoin, Onyx, Surgarchain, Sprint, Yenten, Arionum, MintMe, and Bitweb.
Since the scammers carefully mask the addresses of their cryptocurrency wallets, researchers have not been able to understand how much profit Purpleurchin’s campaign brings to its operators.
However, the damage that manners produce to GitHub is amenable to change: Sysdig analysts estimate it at $15 per month per account. For Heroku and Buddy, the damage is between $7 and $10 per month per account.
Since the cryptocurrencies mined by attackers can hardly be called profitable, Sysdig analysts suggest that either the operation is at an early experimental stage, or fraudsters are even trying to carry out a 51% attack.





