Exploit for 0-day Vulnerability in Atlassian Confluence
PoC exploits have appeared for the critical vulnerability CVE-2022-26134 affecting Atlassian Confluence and Data Center servers.
This bug allows unauthenticated attackers to create new administrator accounts, execute commands, and take over someone else’s server.Let me remind you that the vulnerability was discovered last week by Volexity experts. CVE-2022-26134 is an RCE vulnerability that does not require authentication and uses OGNL injections.
Let me also remind you that we wrote that Atlassian developers found critical vulnerabilities in Jira Service Desk.
Atlassian developers reported that the vulnerability is confirmed in Confluence Server 7.18.0, while Confluence Server and Data Center 7.4.0 and higher are also vulnerable.

Patches have already been released for the bug. If patching is not possible due to the severity of the problem, we recommend users to either restrict access to Confluence Server and Data Center from the Internet, or temporarily disable them altogether.
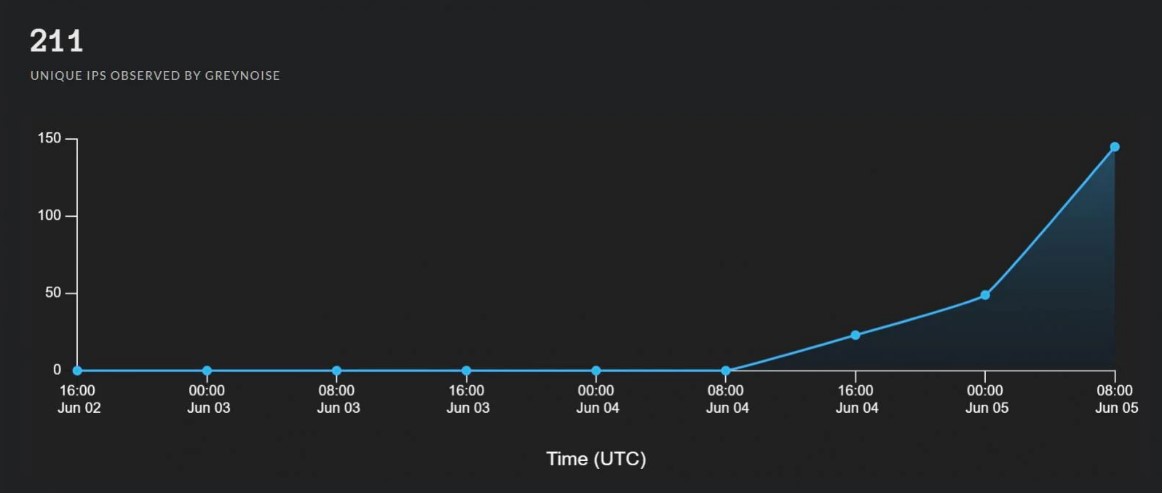
Earlier last week, attacks on a fresh bug were reported. Analysts wrote that behind these attacks there are numerous malefactors from China. Now the number of attacks has increased, and at the end of last week, a PoC exploit was published, which was widely distributed on the network over the weekend.
Exploits circulating on the web make it easy to create new administrator accounts, force DNS queries, collect system information, and create reverse shells.