Back in September 2019, an unknown information security researcher discovered a dangerous 0-day vulnerability in vBulletin versions 5.0 to 5.4. The bug received the identifier CVE-2019-16759 and allowed executing arbitrary PHP commands on a remote server (without having to log in to the forum itself).
Although a fix for this bug was released just a day after the issue was disclosed, not everyone managed to install the updates in time. As a result, the vulnerability affected the official Comodo forums, the ZoneAlarm forums, as well as the Italian and Dutch resources for sex workers (in these countries, prostitution is legal).It seems that more than six months have passed since the discovery and fix of the bug, and now the vulnerability can hardly pose a threat to anyone. However, over the weekend, cyber security expert Amir Etemadieh said in his blog that the patch for the CVE-2019-16759 problem is ineffective, it can be bypassed, and the bug can still be exploited by attackers.
To prove his point, the expert published three PoC exploits for the vulnerability: in Bash, Python and Ruby. Essentially, these exploits allow remotely executing commands with a simple one-line command sending a POST request to the vBulletin server.
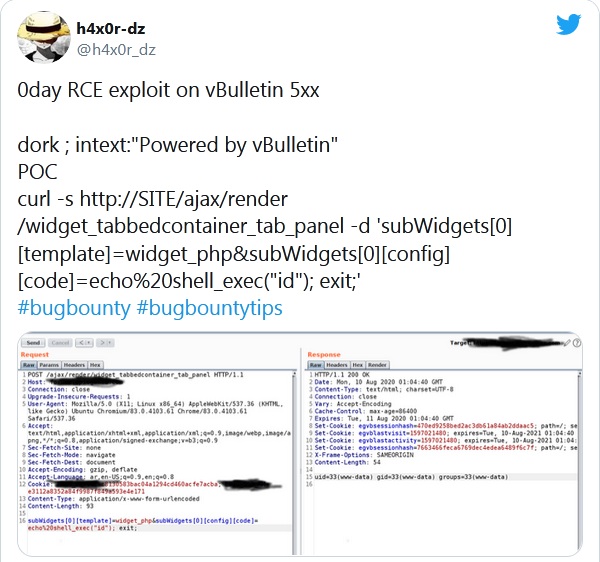
However, the researcher did not consider it necessary to notify the vBulletin developers that the problem is still urgent. That is, at the time of publication of the article and new exploits, there was no patch for the problem yet.
As a result, information about the old-new 0-day vulnerability quickly spread to Reddit, Twitter, Discord, other social networks, as well as in hacker communities. Of course, the attacks began immediately. As a result, at least one forum was hacked using this vulnerability: it is very ironic, but was damaged forum of the information security conference DEF CON, which ended over the weekend.
“A new vBulletin Zero Day got dropped yesterday by @Zenofex that revealed the CVE-2019-16759 patch was incomplete – within three hours forum.defcon.org was attacked, but we were ready for it. Disable PHP rendering to protect yourself until patched!“, — wrote researcher Jeff Moss in his Twitter.
Currently the vBulletin developers have already prepared a patch for the problem and recommend installing it as soon as possible. If the installation of the fix is impossible for some reason, Amir Etemadieh advises to go to the conference settings, and there disable PHP, Static HTML and the Ad Module rendering. This should also protect against possible attacks.
Recall, by the way, that not only forums suffer from hackers, an ideologically similar platform, the famous Reddit, recently suffered from hacker attacks, and the attackers were supposedly ardent fans of Donald Trump.





